A company’s internal server has been flagged for unusual network activity, with multiple outbound connections to an unknown external IP. Initial analysis suggests possible data exfiltration. Investigate the provided network logs to determine the source and method of compromise.
Question 1
What is the FTP password?
- By filtering out FTP traffic in the packet capture, we can see the attacker authenticated successfully with this password.
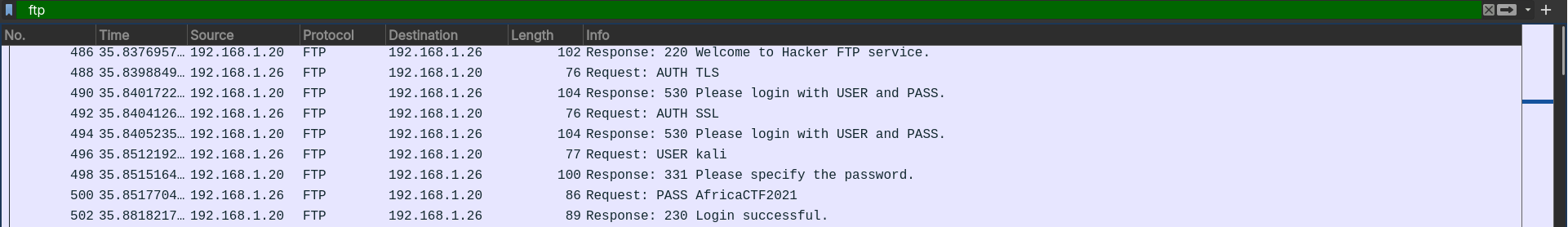
Answer: AfricaCTF2021.
Question 2
What is the IPv6 address of the DNS server used by 192.168.1.26?
- Under DNS Analysis, there are only answers from 2 IPs, one is IPv4 and one is IPv6.
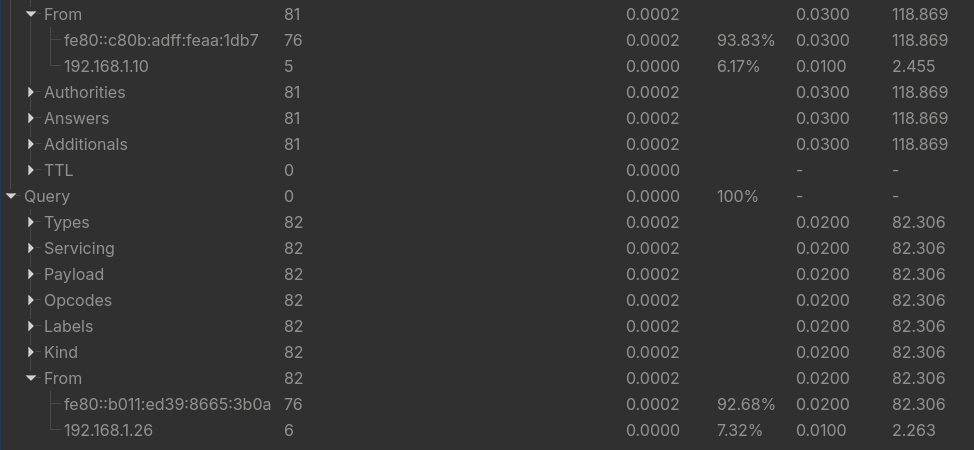
Answer: fe80::c80b:adff:feaa:1db7.
Question 3
What domain is the user looking up in packet
15174?
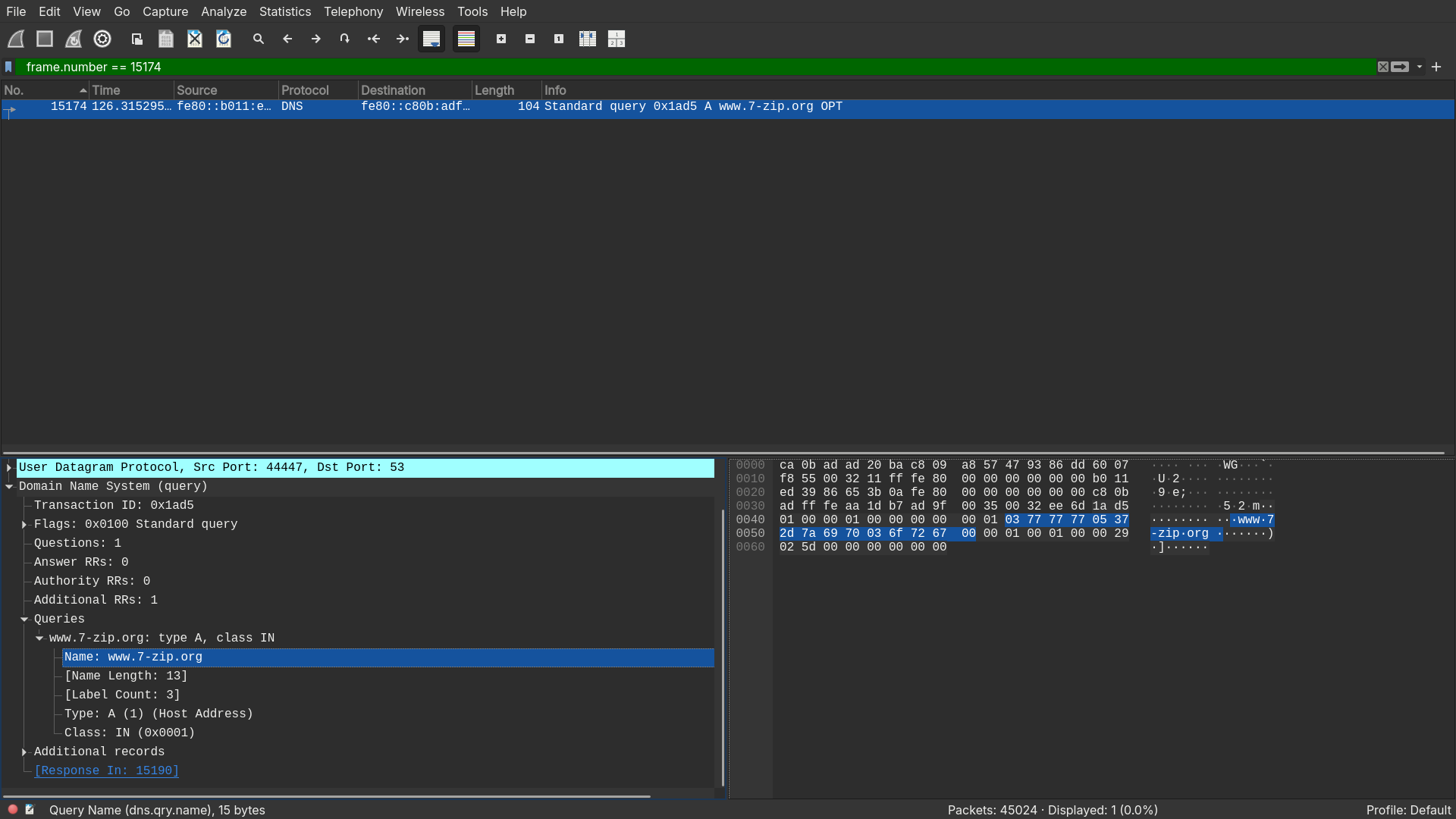
- In frame number
15174, the user is looking upwww.7-zip.org
Answer: www.7-zip.org.
Question 4
How many UDP packets were sent from
192.168.1.26to24.39.217.246?
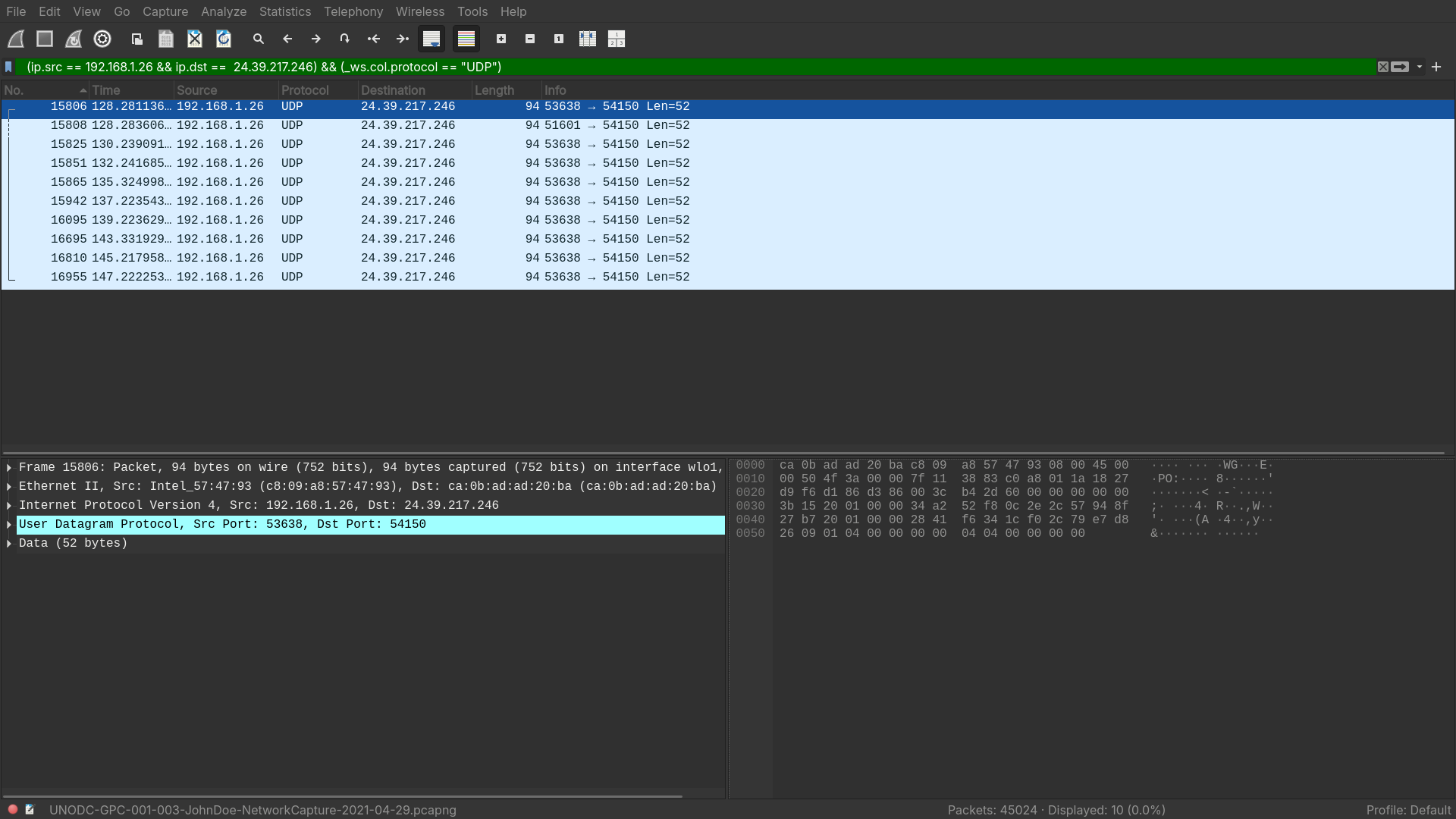
- After filtering, there are 10 UDP packets sent to
24.39.217.246
Answer: 10.
Question 5
What is the MAC address of the system under investigation in the PCAP file?
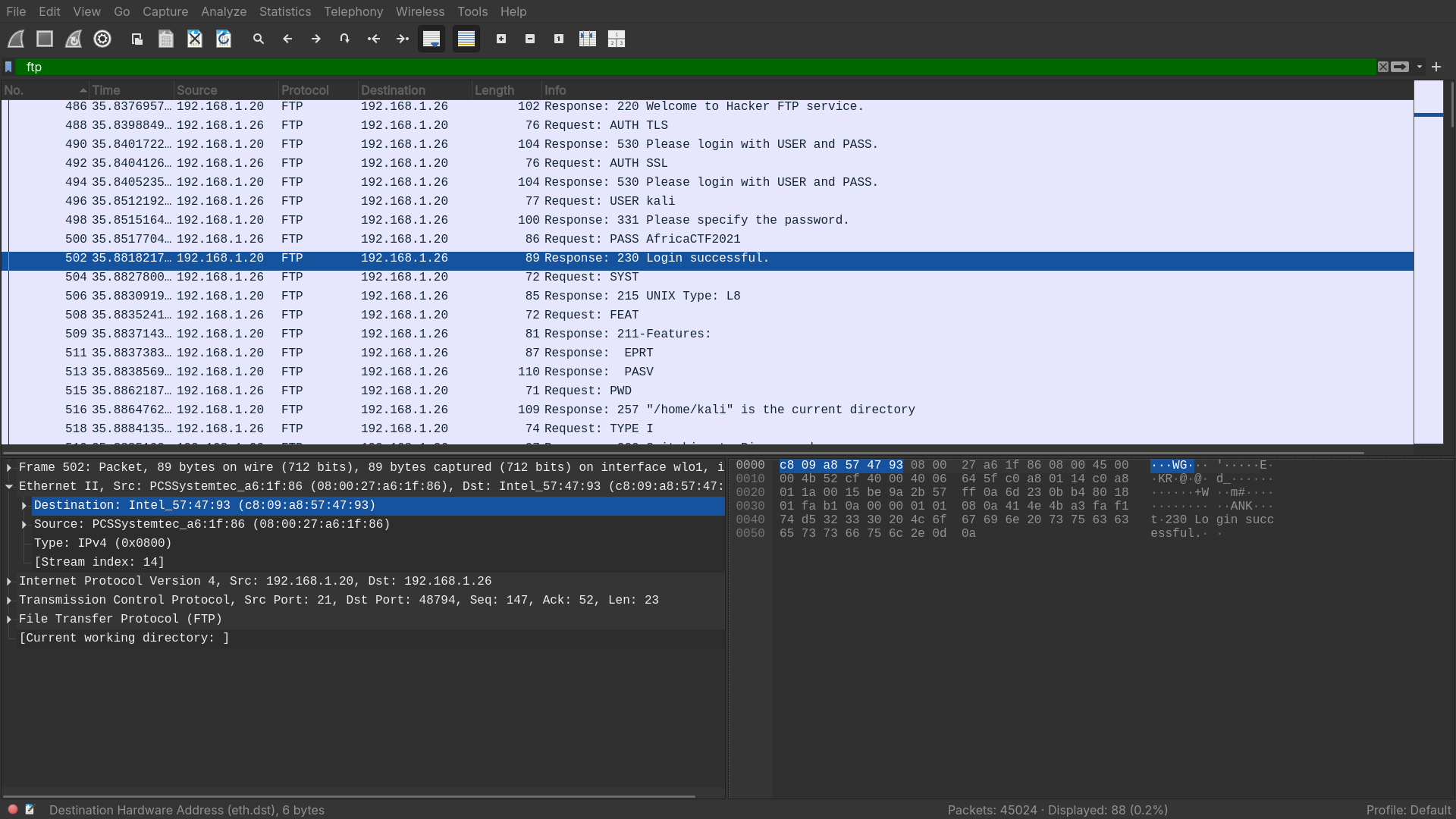
- The attacker compromised the device with the MAC address
c8:09:a8:57:47:93with FTP.
Answer: c8:09:a8:57:47:93.
Question 6
What was the camera model name used to take picture
20210429_152157.jpg?
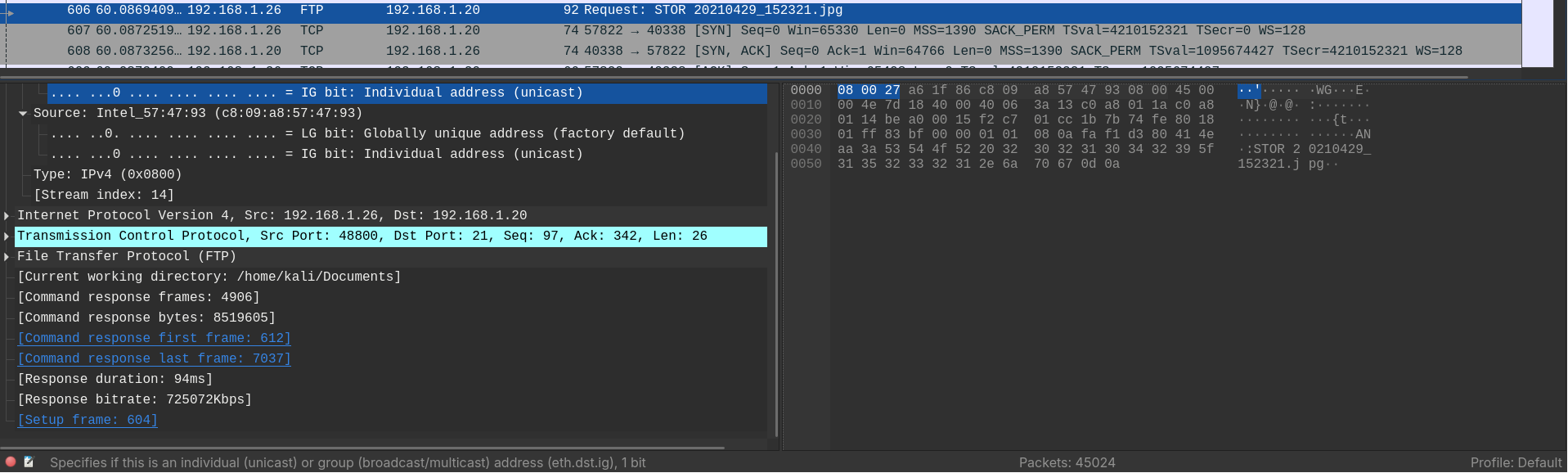
- The attacker made an FTP request for
20210429_152157.jpg. The camera model may be stored as metadata, which could be stored at the start of the files. Which we can find by inspecting the first few transfered data traffic.
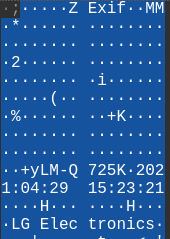
Answer: LM-Q725K.
Question 7
What is the ephemeral public key provided by the server during the TLS handshake in the session with the session ID:
da4a0000342e4b73459d7360b4bea971cc303ac18d29b99067e46d16cc07f4ff?
- Filtering out the traffic, we get:
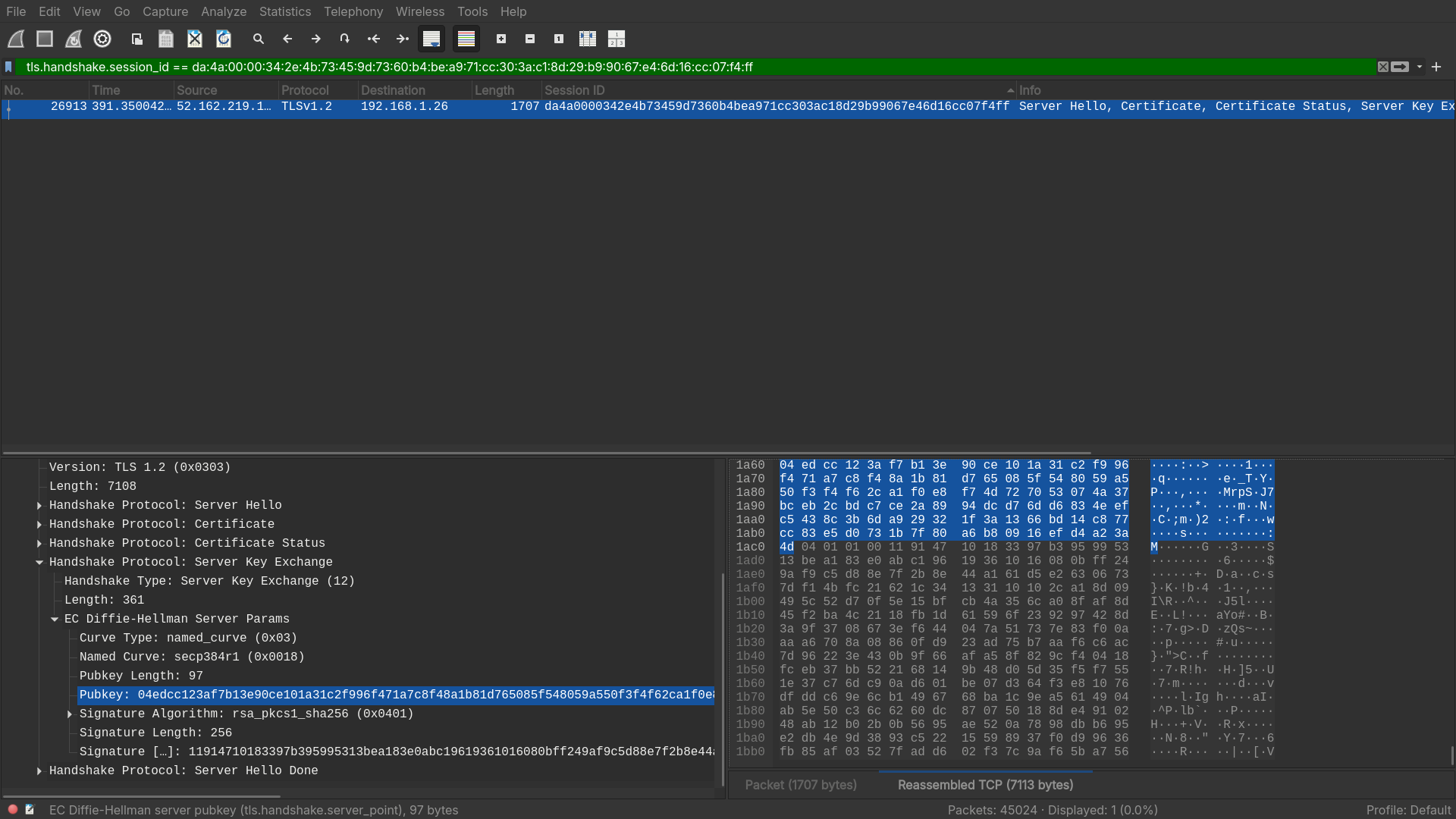
Answer: 04edcc123af7b13e90ce101a31c2f996f471a7c8f48a1b81d765085f548059a550f3f4f62ca1f0e8f74d727053074a37bceb2cbdc7ce2a8994dcd76dd6834eefc5438c3b6da929321f3a1366bd14c877cc83e5d0731b7f80a6b80916efd4a23a4d
Question 8
What is the first TLS 1.3 client random that was used to establish a connection with
protonmail.com?
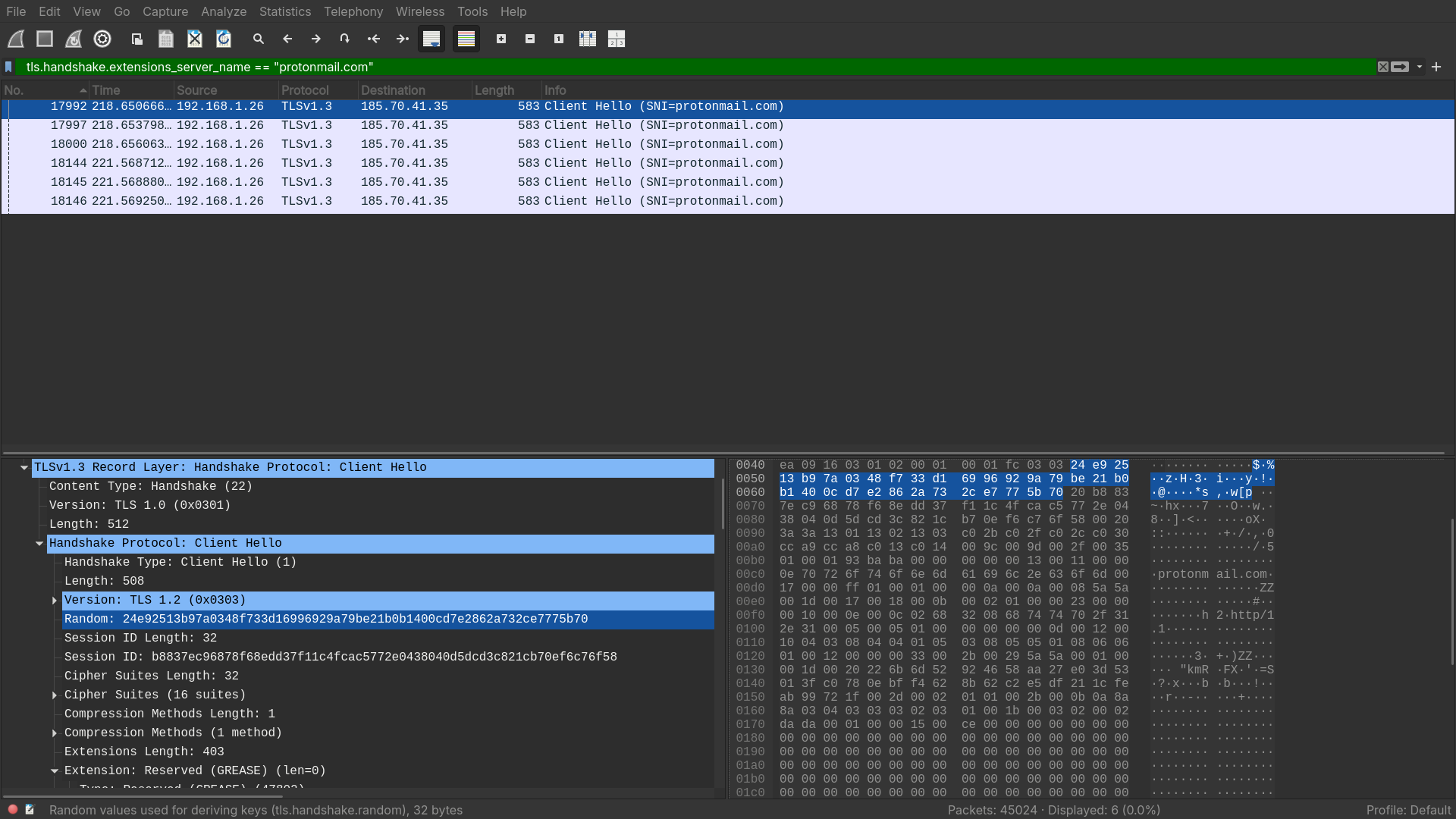
Answer: 24e92513b97a0348f733d16996929a79be21b0b1400cd7e2862a732ce7775b70
Question 9
Which country is the manufacturer of the FTP server’s MAC address registered in?
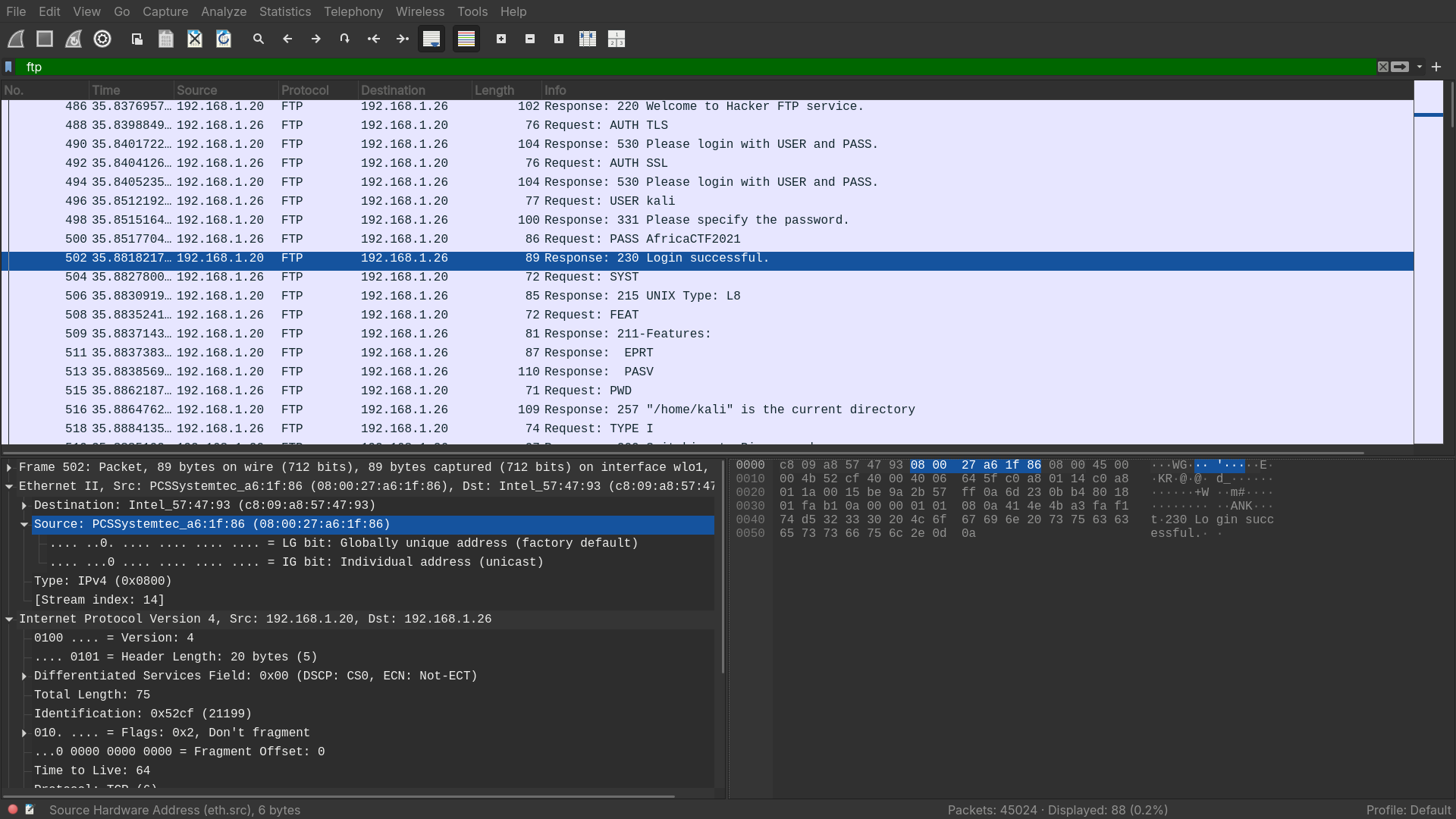
- From the response, we know that the MAC address of the FTP server is
08:00:27:a6:1f:86, a quick lookup using https://maclookup.app/search/result gives us:
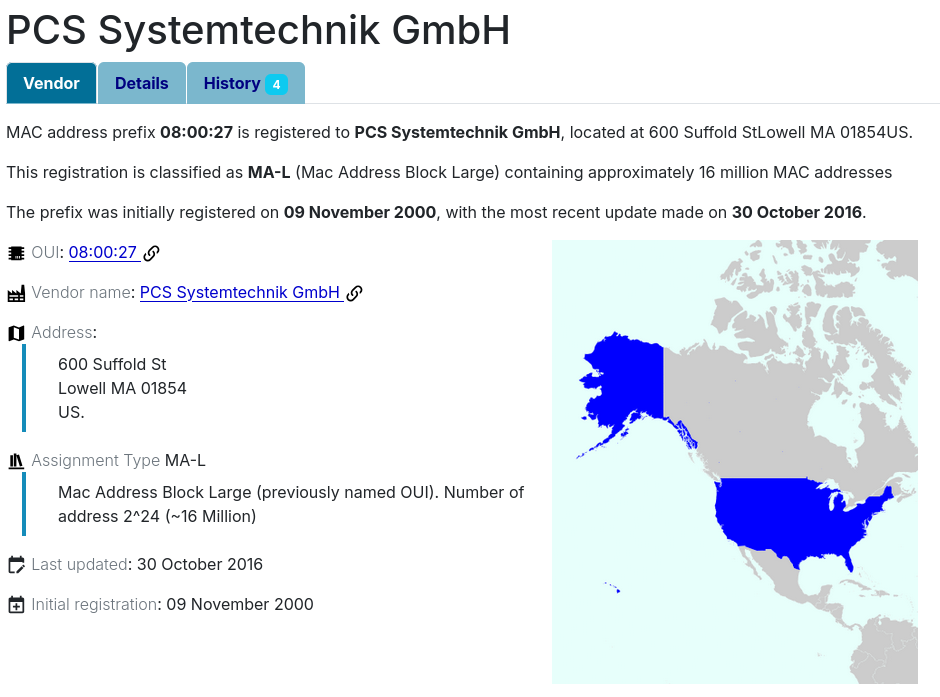
Answer: United States.
Question 10
What time was a non-standard folder created on the FTP server on the 20th of April?
- Filtering out the FTP traffic, we can see the attacker made some LIST request, with one of them got a response in frame
530
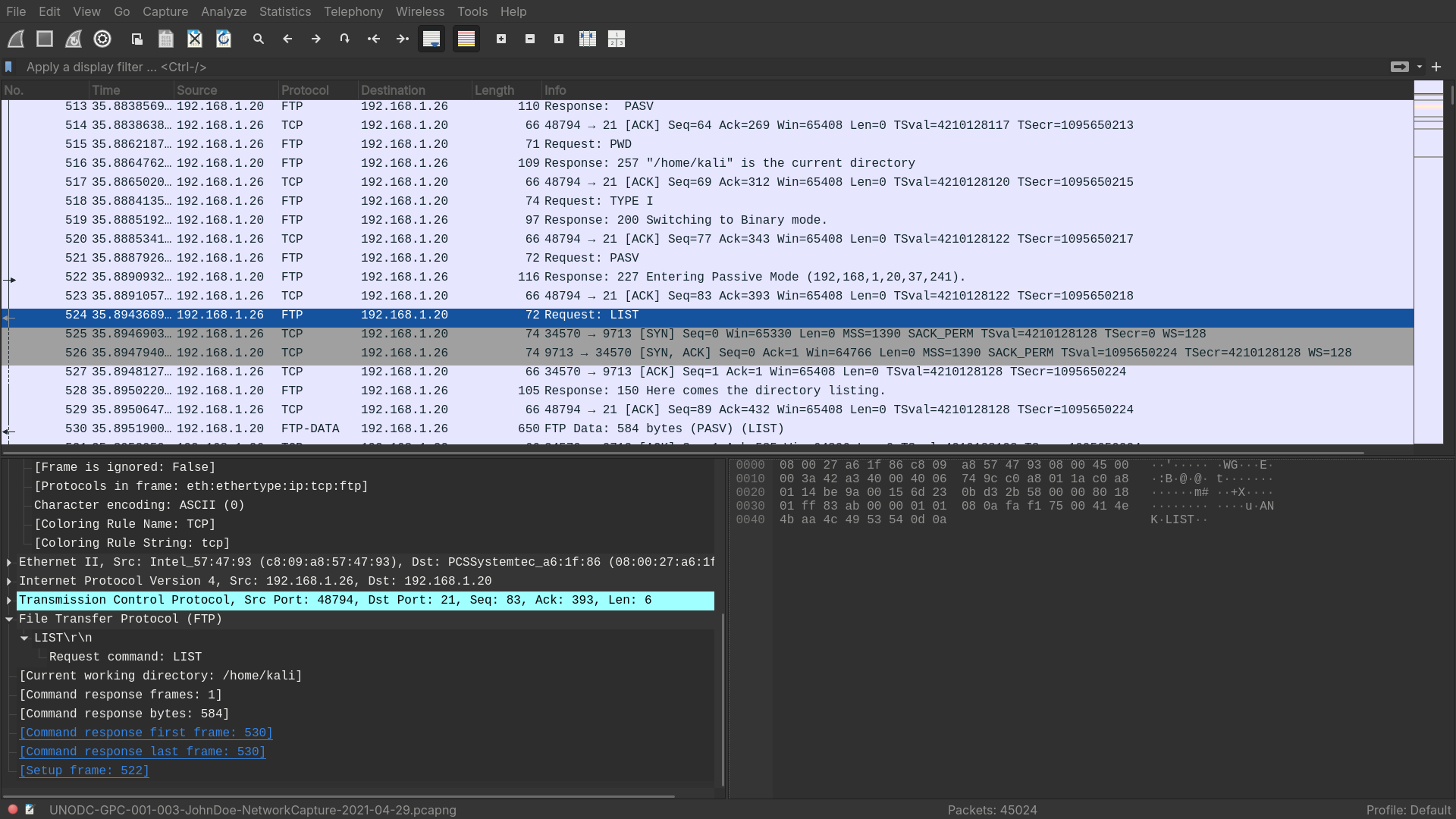
- Inspecting frame
530, we are able to see the directory listing of the FTP server.
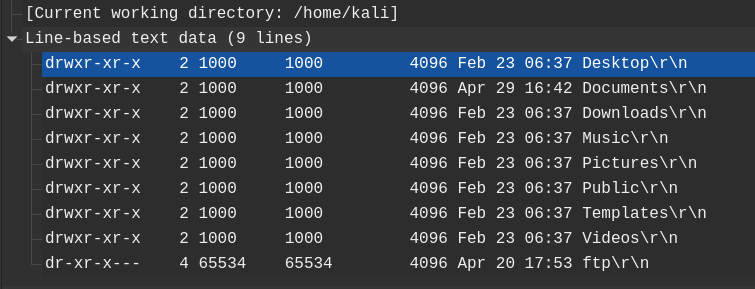
- The non-standard folder here is
ftpwhich was created on April 20th at17:53.
Answer: 17:53.
Question 11
What URL was visited by the user and connected to the IP address
104.21.89.171?
- The user made a request to
104.21.89.171at frame26257
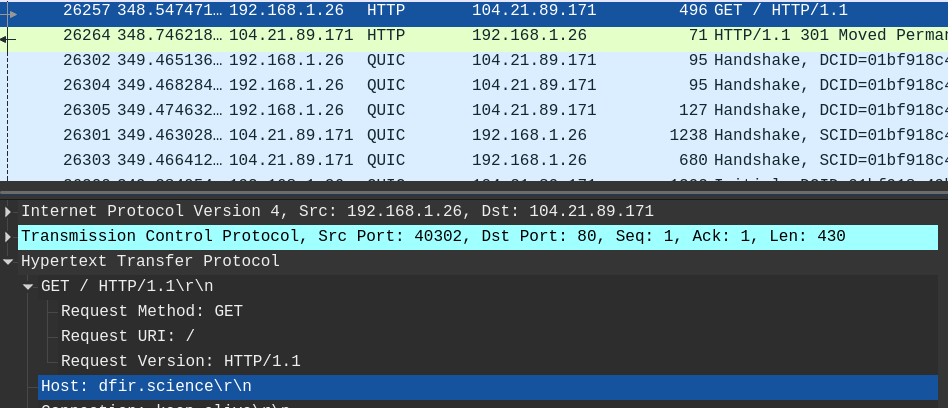
- The host for this GET request is
dfir.science
Answer: http://dfir.science/.